In this article, we dive into the inner workings of AsyncRAT. This Remote Access Trojan (RAT) has seen a staggering 20% surge in its activity during the last quarter, as reported by the Spamhaus report.
We’ll explore diverse decryption methods for the AsyncRAT configuration and explore the AES Salts used in various files.
What is AsyncRAT?
AsyncRAT is a Remote Access Tool (RAT) designed to remotely monitor and control other computers through a secure encrypted connection. It is an open source remote administration tool, however, it could also be used maliciously because it provides functionality such as keylogger, remote desktop control, and many other functions. (Source: Malpedia)
Delivery Methods: How Malware Spreads
Spear-phishing, malvertising, exploit kit, and other techniques serve as delivery methods for this malware.
AsyncRAT Config Decryption via Static Extractors
Let’s dig deeper into decrypting the AsyncRAT configuration with static extractors like CyberChef Recipe and Python script.
CyberChef Recipe
One of the most efficient ways to decode the AsyncRAT config is by using the CyberChef Recipe developed by Srujan Kumar. I have made few modifications to existing recipe which support new AsyncRAT files.
The updated recipe, available on GitHub, works by decoding the AsyncRAT config. You need the code, salt, and variable name that stores the AES key. My research suggests that the current AsyncRAT samples predominantly use two salts.
For a step-by-step guide to use CyberChef to decrypt the AsyncRAT, check this article.
Python Script
Abdallah Elnoty has developed a small python script to decode the config. You can find all the details in this article (Feb 2022).
Dynamic Approach: Reflection in PowerShell
For those who prefer a more dynamic approach, @vinopaljiri has shared an innovative technique for config decoding. This method involves using reflection and PowerShell to load the binary and then invoke the InitializeSettings method, providing a quick and efficient approach. You can find more details here.
AsyncRAT Analysis: AES Salt
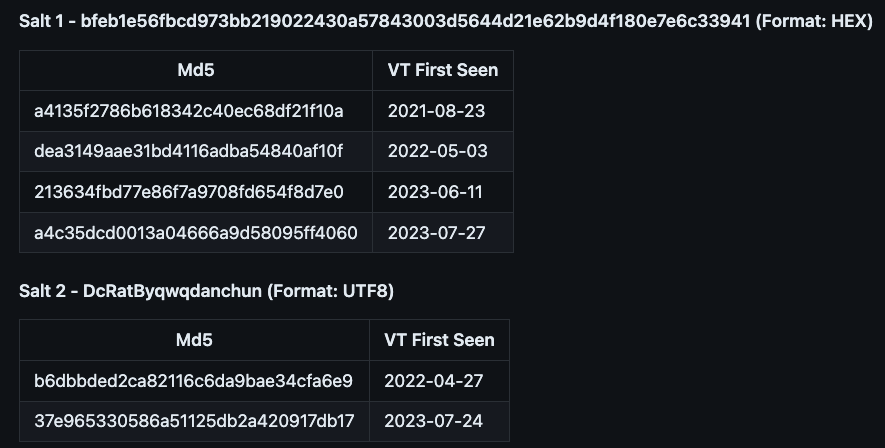
In my analysis of approximately 10-20 files, , I encountered only two distinct salts for AsyncRAT. You can find more details on my Github page.
Salt 1: bfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 (Format: HEX)
This salt is referenced in the AsyncRAT source code available on Github (Last commit: May 10, 2020). It is also utilized in Quasar RAT 1.3, as indicated in the QuasarRAT-Analysis from December 1, 2020.
Salt 2: DcRatByqwqdanchun (Format: UTF8)
This salt is also used by DcRat malware (First commit: Mar 20, 2021).
Conclusion
These techniques are still effective on unpacked files, with some minor modifications. In the next blog post, we will delve deeper into CyberChef recipe and dynamic approach. Stay tuned!
1 Comment. Leave new
[…] For those keen on exploring more about config decryption techniques, I recommend diving into my previous article. […]