We will concentrate on malicious macro embedded in Emotet downloader office documents and see how to deobfuscate the macro code. In the next post we will deobfuscate the PowerShell executed by Word Doc.
Why do we need to do this?
- Malicious code embedded in macro instead of exploit
- Clean up the code, so we can analyse the macro easily
Sample
You can download the Emotet downloader sample from zip archive 2018-05-04-Emotet-malware.zip mentioned in this link / Virustotal.
Important Macro concepts
Macros are written in VBScript commands. The steps to show the developer tab varies based on the Office version, check this link for more details.
Sub Procedure
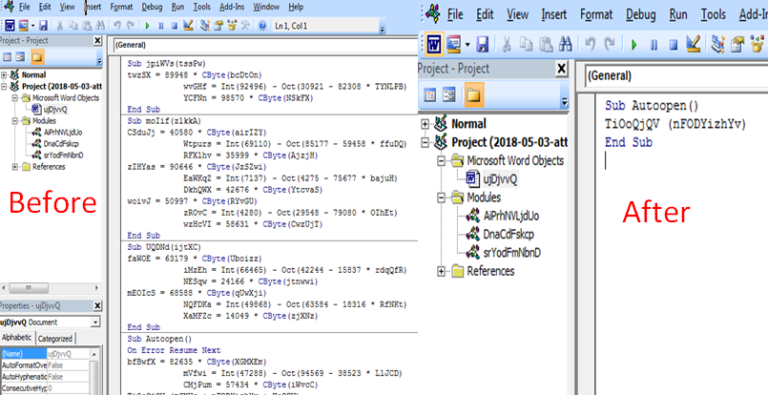
A Sub procedure is a series of Visual Basic statements enclosed by the Sub and End Sub statements that performs actions but doesn’t return a value. For more details check this msdn link. This following procedure contains junk code which is not used anywhere.
Sub jpiWVs(tssPw)
twzSX = 89948 * CByte(bcDtOn)
wvGHf = Int(92496) - Oct(30921 - 82308 * TYNLPB)
YCFNn = 98570 * CByte(NSkFX)
End Sub
Function
A Function procedure is a series of Visual Basic statements enclosed by the Function and End Function statements. A Function procedure is similar to a Sub procedure, but a function can also return a value. For more details check this msdn link.
Function nFODYizhYv()
On Error Resume Next
HaPTn = 36440 * CByte(cGdhi)
AqKKP = Int(78184) - Oct(38288 - 29334 * FjYvSt)
GJKXZG = 1995 * CByte(GZUcj)
......
MUtvc = 12179 * CByte(GKtld)
JLfpah = Int(41681) - Oct(37691 - 32289 * NGzQXX)
LPHts = 34930 * CByte(wKlPaU)
End Function
On Error Resume Next
It means that whenever there is any error in the program then continue to the next line. Due to this statement malware authors can write junk statements to obfuscate code to make our(or security product) analysis difficult .
Autoopen
One of the important functions used in the malicious macro is Autoopen(). This function execute when we open a document, so malware execution starts from the function.
Autopen function present in this word doc
Sub Autoopen()
On Error Resume Next
bfBwfX = 82635 * CByte(XGMXEm)
mVfwi = Int(47288) - Oct(94569 - 38523 * LlJCD)
CMjPum = 57434 * CByte(iWvcC)
TiOoQjQV (tCXUs + nFODYizhYv + KsQPV)
...
End Sub
Debug.Print
We can print any value of variable by adding Debug.Print variable_name, it will display the output in View-> Immediate Window (Ctrl+G)
Shell
Shell function is used to run any code, for more details check this link msdn link. This function is used to execute the malicious power shell cmd to download and execute Emotet malware.
[Shell] ZHBuq + Chr(vbKeyC) + qFkOSjfj + qjXrchNTBZRhNs + sEPXQbb, ciXcjw + 0 + ciXcjw
Mid
MID function extracts a substring from a string (starting at any position). For more details check this link.
Deobfuscation
This macro is heavily obfuscated with junk code and random variable/function name. For deobfuscation we just need to check if the variable/function is used in the program. This macro uses the StrReverse and Mid function on different strings to build the malicious PowerShell code.
Video Tutorial
Let’s see how to use the above concepts to deobfuscate the macro. In this post we will not concentrate on the PowerShell part, we will just deobfuscate the macro. Check this article which explain how to deobfuscate and extract CC
In the next post we will concentrate on the deobfuscation of PowerShell.