Qealler is heavily obfuscated Java based Infostealer which is quite active based on ANY.RUN submission. This will be a three part blog series, this post will focus on Qealler/Pyrogenic static analysis, next part 0x2 we learn unpacking using Java agent and in the last part 0x3 we find similarity between Qealler/Pyrogenic variants based on static code analysis . You may download the BankPaymAdviceVend_LLCRep.jar from ANY.RUN (MD5: F0E21C7789CD57EEBF8ECDB9FADAB26B) and follow along or download the latest Qealler sample from ANY.RUN submission.
CONTENTS
Overview
It’s currently targeting different regions e.g. Australian companies[1], Africa and the Middle East[2] based on the references. I will be using Bytecode Viewer to decompile Jar using FernFlower Java Decompiler. Let’s start with quick dynamic analysis. Our main goal for the blog series is to unpack this jar so we can analyse the capability and compare it with Qealler.
Quick Dynamic Analysis
- Connect to CC 157.245.160[.]150 at port 80 and create the below process.
cmd.exe /c chcp 1252 > NUL & powershell.exe -ExecutionPolicy Bypass -NoExit -NoProfile -Command - - Drop these two clean files sqlitejdbc.dll (MD5: a4e510d903f05892d77741c5f4d95b5d) and jnidispatch.dll (MD5: d2f0da769204b8c45c207d8f3d8fc37e) but it deletes these two file before exiting.
- Connect to bot.whatismyipaddress.com to get the public IP of the infected system.
- Steal credential from different applications
Packed Pyrogenic static analysis
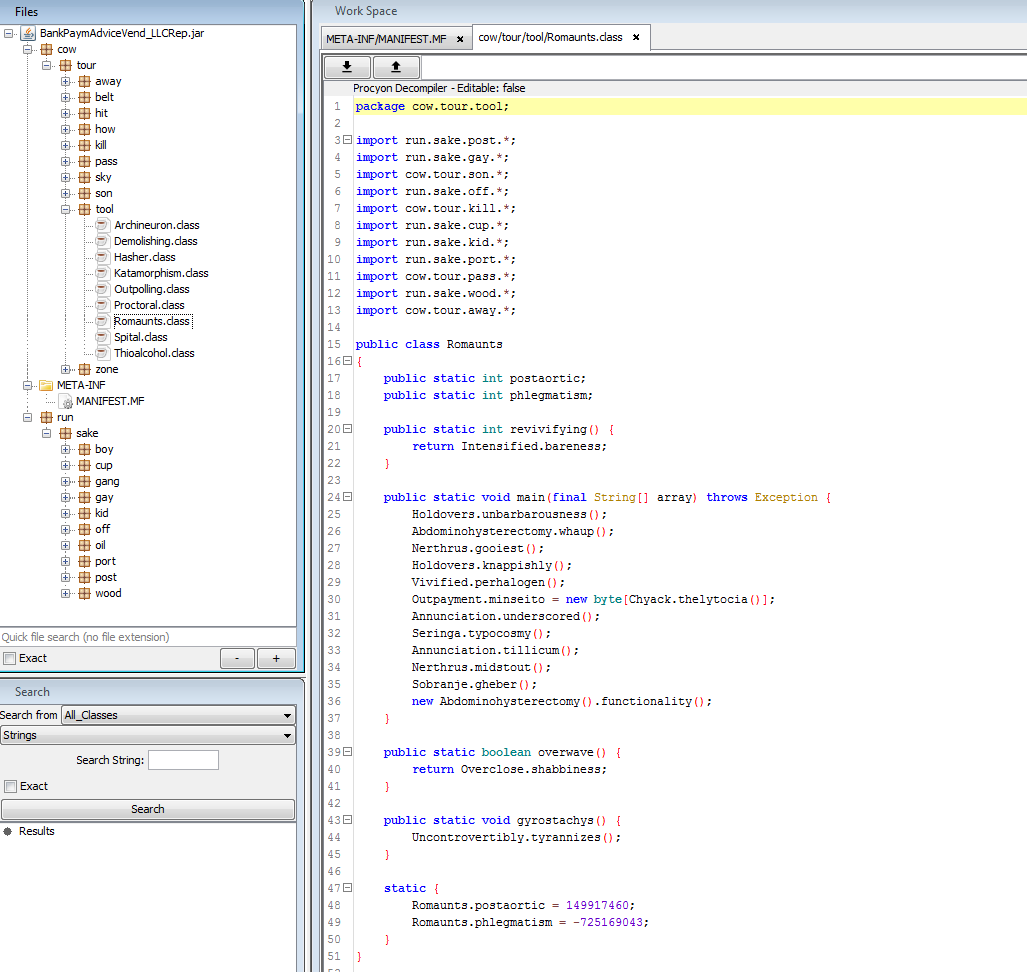
- Open the jar file in BCV (Bytecode Viewer), you will see multiple class files in different packages. Below pic shows the main entry point of the jar file.
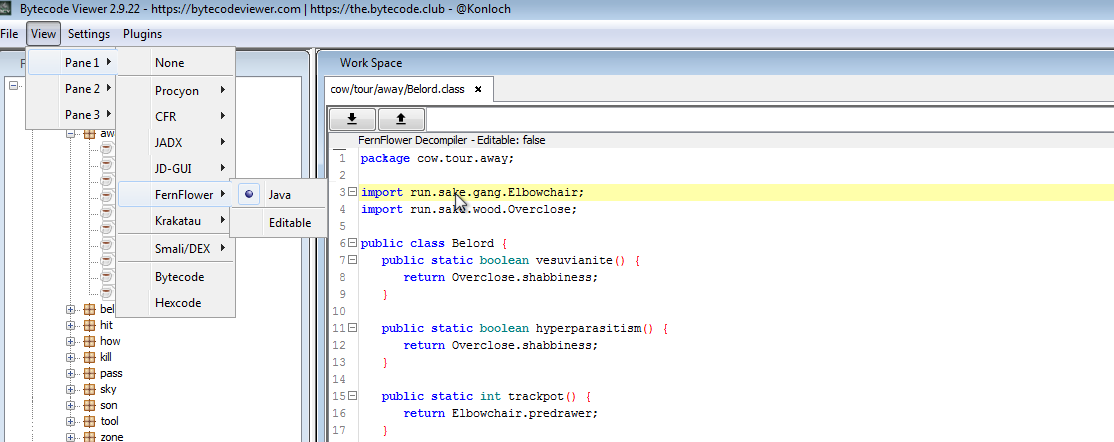
- For this sample, I found out that FernFlower decompiled the source code correctly. Select View -> Pane 1 -> FernFlower -> Java in BCV as shown below.
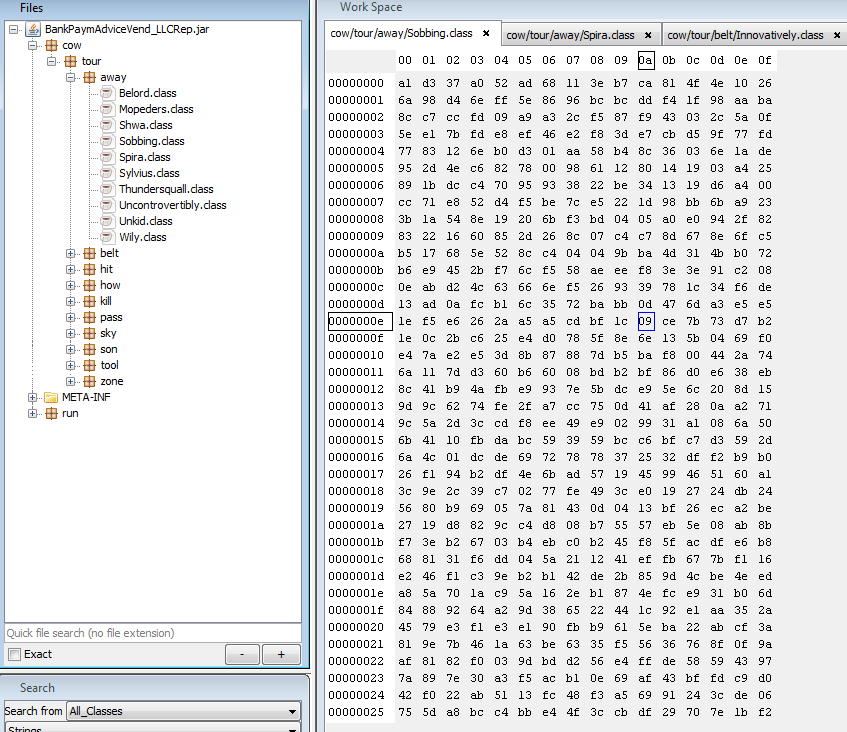
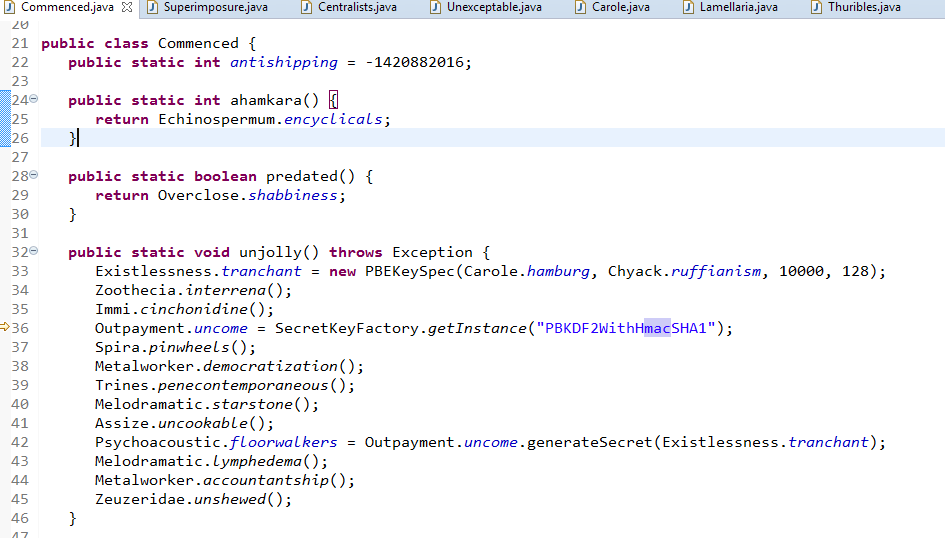
- If you browse the different class files in BCV, you will find many encrypted class files which don’t translate to Java src code. e.g. one of them is shown below
- Based on the above encrypted class file, you can guess that there should be some decryption algorithm used to decrypt those files.
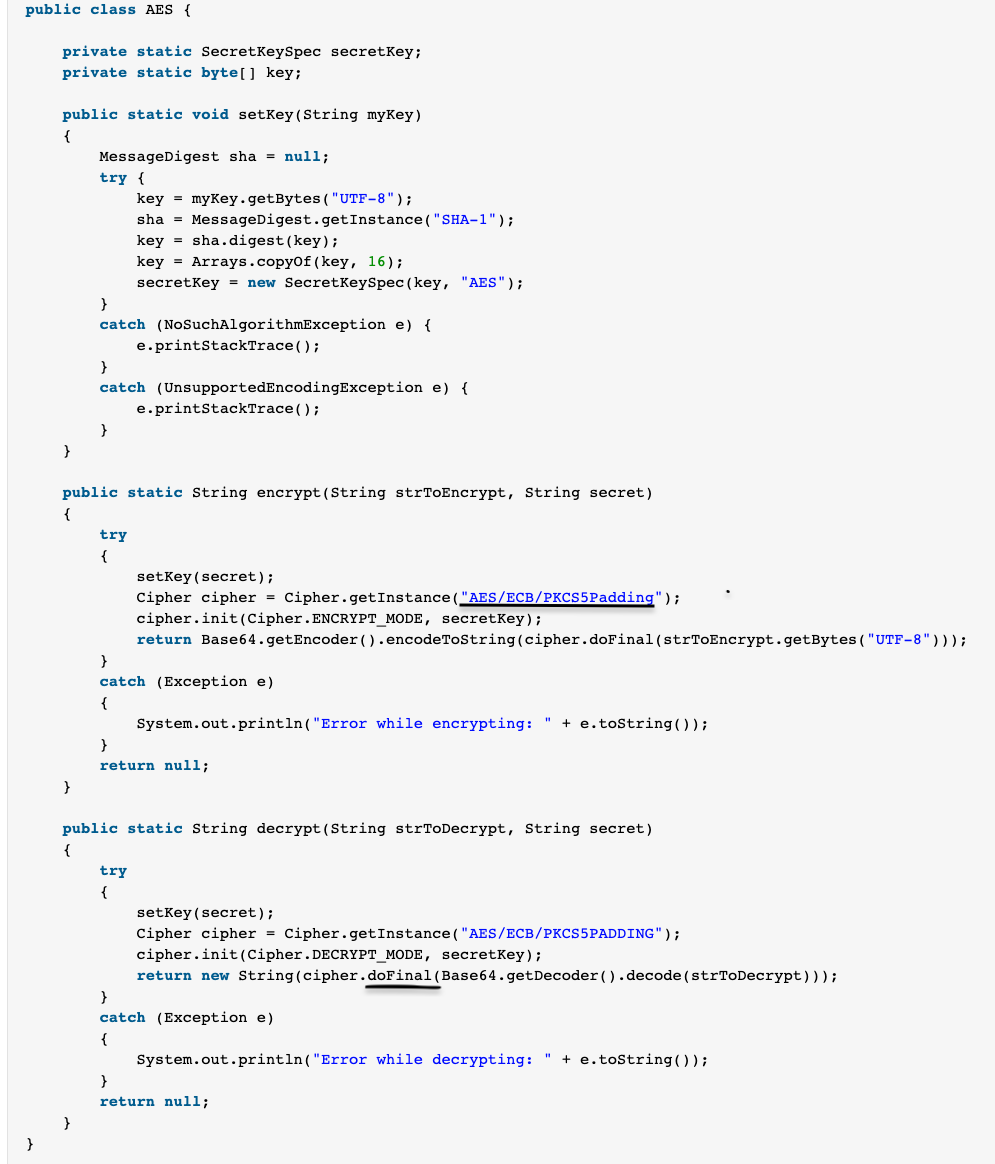
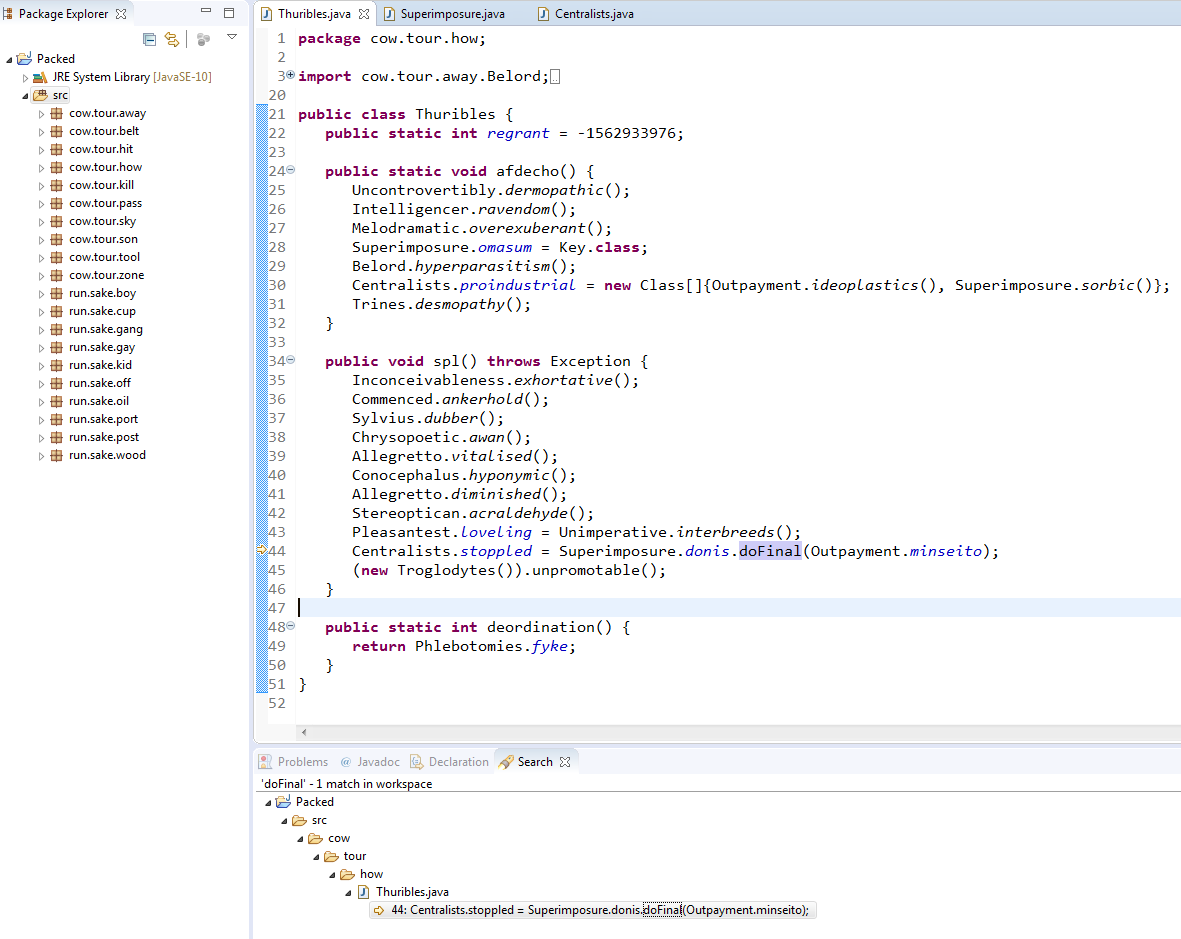
- Decryption algorithms can be custom or well known e.g. AES. Study this example java code [3] which encrypt/decrypt using AES. Some of the keyword mentioned in the above java code e.g. getInstance can help us to find the encryption algorithm and doFinal can point to final decryption result.
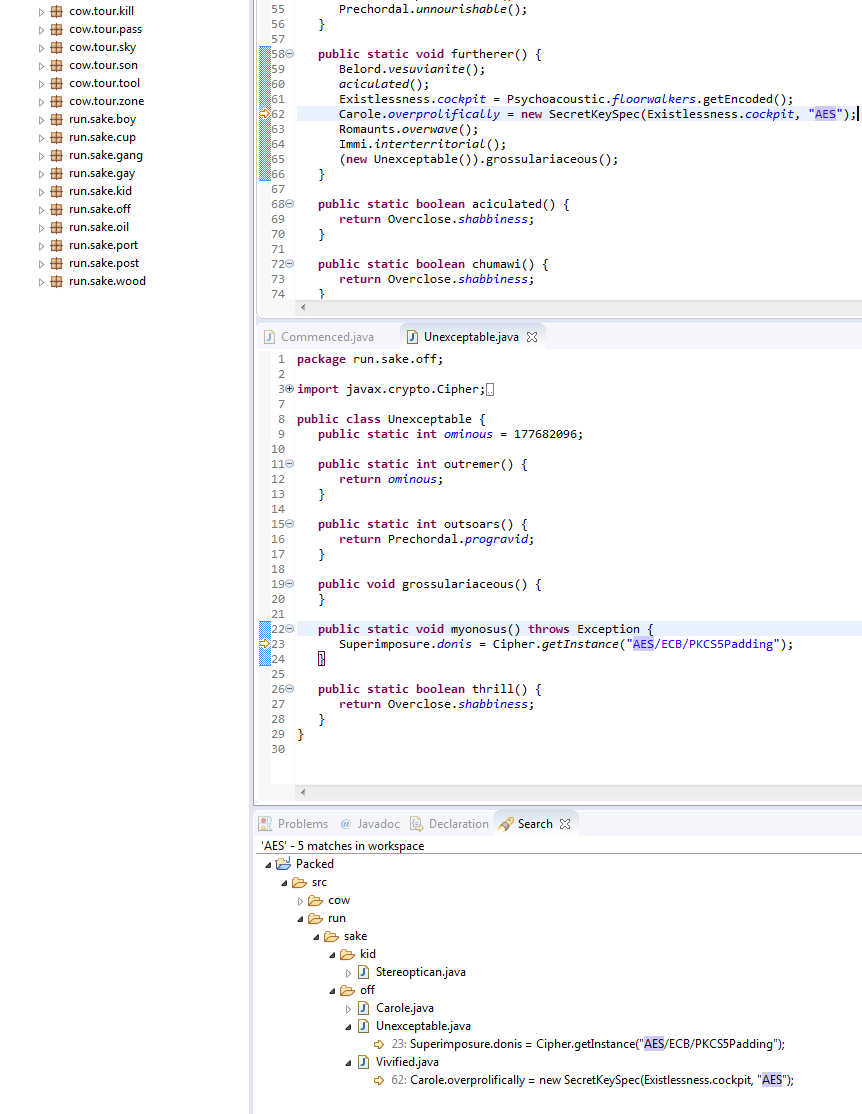
- Let’s search for AES references after importing the decompiled src code to Eclipse IDE.
- Based on the above images which shows multiple references, we can confirm that this sample uses the algo “AES/ECB/PKCS5Padding” and key may be generated using “PBKDF2WithHmacSHA1” . So it confirmed that it doesn’t use any custom decryption algorithm.
- We can add our code to write the data to file after doFinal call and execute the sample in IDE to get the dumped class file Then we can decompile the class file using BCV and continue analysis. But it can be multiple layer obfuscation which can make our analysis harder and slower.
Conclusion
This above static analysis method to find the encryption routine and interesting breakpoint (doFinal) while debugging is very useful in Java Malware analysis. Using this approach you will not miss any code path but this requires more time and effort. So in the upcoming part 0x2 , we will unpack this malware using Java agent which will speed up our analysis.
3 Comments. Leave new
[…] how and when we can use Java agent to quickly unpack the Pyrogenic Infostealer. In the earlier post Pyrogenic Infostealer static analysis – Part 0x1 we statically analysed the Pyrogenic/Qealler Infostealer but this require more time and effort. […]
[…] this last part, we will compare Old Qealler with new Qealler/Pyrogenic variant. The previous posts Pyrogenic Infostealer static analysis – Part 0x1 & Unpacking Pyrogenic/Qealler using Java agent -Part 0x2 went through the latest […]
[…] dd skip=0xc600 if=06-01-20.jar of=extracted_ratty.jar bs=1 If you are new to Java reversing or Bytecode Viewer, you may want to check this Pyrogenic/Qealler Infostealer static analysis – Part 0x1. […]